Which is not typical for a local network. What are local and global computer networks? Data transfer via them is carried out in two ways
It's hard to imagine that you have never heard anything about personal computer networks. You may even know that there are local and global networks. The most erudite among you know words like Ethernet and repeater. However, when presenting the material, we will assume that you have never worked on a computer network before. Accordingly, you will not be required to have any special knowledge, except, of course, that which you acquired from the first volumes of our series of books “Personal Computer - Step by Step”.
1.1. Why are computers connected into a network?
If you only have one personal computer, no modem and no desire to purchase one, you will never be able to experience the benefits that computer network. However, if your office has several computers or there is a need to transfer data to geographically remote branches, you should hardly neglect network technologies.
Let's try to answer the question posed in the section title: why are computers connected?
Obviously, in order to be able to transfer data from one computer to others. But this is too general a formulation. It is not yet clear how the ability to transfer data from one computer to another can save time and money (especially considering that networking requires additional costs for network hardware and software).
Let's try to prove that network technologies save money, and a lot of it. To do this, we will briefly consider possible areas of application of computer networks.
In this book we will deal with local networks.
Local networks are networks that connect nearby computers (in the same room, in one or more nearby buildings). In this case, dedicated communication lines belonging to the same company as the computers are used to connect computers.
As for global networks, there are no restrictions on the distance between computers. There are global networks that connect computers in different countries and on different continents. Of course, no small or medium-sized company (except a telephone company) can own intercontinental communication lines. To create global networks, you have to rent telephone or satellite communication lines.
Local networks are characterized by a high speed of information transfer between computers, reaching 10 or even 100 Mbit per second. The data transfer speed in global networks is low and when using telephone lines it can be 2400-28800 bits per second.
The areas of application of local and global networks are different, but both are significant achievements in the field of computer technology, and therefore deserve the closest attention.
Printing documents
Any office needs to print certain documents. Despite the widespread introduction of the so-called “paperless” technology, the number of printed documents not only has not decreased, but has even increased.
If you care about the prestige of your company, all its internal and external documents should be printed on high-quality laser printer.
For simple documents, you can use a relatively cheap printer that costs a few hundred dollars. In some cases, a color printer is needed. If you are engaged in publishing, you need an expensive laser printer, the cost of which can amount to thousands of dollars.
Of course, there is no point in buying several expensive laser printers, one for each computer. Not every company can afford such costs. Therefore, usually only one or two printers are purchased.
But how to connect one printer to several computers at once?
There are several possibilities.
Firstly, you can buy a special switch that connects on one side to the printer, and on the other to several computers (Fig. 1.1).
Rice. 1.1. Connecting a printer via a switch
Obviously, this solution is suitable only in the simplest cases, when all computers are in one room, and a printer is installed in the same room. If there are a lot of computers, a queue of people wanting to use the printer will gather around the switch.
Secondly, you can connect the printer to only one computer. If a user who does not have a printer needs to print something, he can write the data to a floppy disk and in this form take it to the owner of the printer.
This method has many disadvantages. For example, the amount of data may be too large to fit on one floppy disk. A user who has a printer connected to his computer is unlikely to be delighted by the fact that company employees will constantly come to him asking him to print a document on a precious laser printer.
The third method assumes the presence of a network of computers (Fig. 1.2).

Rice. 1.2. Connecting the printer to local network computers
Let's leave aside the technical details of connecting computers for now. At this stage, it will be enough for you to know that on a local network computers connect to each other using special network adapters, usually purchased separately.
Network software must be installed on every computer. It provides data transfer in any direction between any computers on the network.
Even though the printer is connected to only one computer, the hardware and network software gives each user access to the printer. The printer becomes a network resource accessible from any computer.
Access to a printer connected in this way is very convenient - the procedure for printing on a network printer is practically no different from the procedure for printing on a local printer (the local printer is connected directly to the computer).
The benefits of using a network to share an expensive printer are most obvious when the computers are scattered across several rooms or floors of a building. Instead of purchasing multiple printers (one per computer or per room), you can get by with just one shared printer, with virtually no impact on productivity. As for the money savings achieved by reducing the number of laser printers, you can determine the effect yourself.
Database
Despite the well-known statement that computers are used mainly as very good and expensive typewriters, there are other, equally useful applications for this device.
The most famous of them is databases. We won't explain to you what it is, at least not in this book. Of course, you know that databases are designed for entering, storing and retrieving a wide variety of information.
In the simplest cases, the entire database is located in the form of one or several files on the disk of one computer. By entering data and requesting necessary information one person is doing it.
However, more often than not, one person cannot cope with the database. Imagine a medium-sized bank's database or an airline's database containing information about available seats and tickets sold.
In this case, several people (or even several dozen or hundreds of people) are involved in data entry and processing. How to create a similar system designed for collective access to a database?
There are two approaches.
The first approach dates back to the times when computers occupied separate rooms, and dozens of specialists from various fields were involved in servicing one computer. It consists of organizing the work of users with one computer in a time-sharing mode.
Previously, a computer was too expensive for only one person to operate. Several terminals consisting of a video monitor and a keyboard were connected to the computer. Specially designed multitasking and multi-user operating systems such as UNIX, MVS and VMS made it possible to share precious computer resources among many users, each of whom solved his own problem.
If you place database files on the disks of such a computer, many users can work with them simultaneously. Thus, the task of organizing collective access is solved quite easily.
The second approach is based on the use of local networks.
In this case, one of the computers is allocated to operate the data management system (DBMS). It is called a database server. The remaining computers connected to the network are called workstations (Fig. 1.3). As the name suggests, workstations are designed for users.

Rice. 1.3. DBMS on local network
Workstations act as intelligent terminals, sending queries to the database, which is physically located on the disk of the DBMS server. The DBMS server processes queries, sending the results of their execution to workstations.
Note that although the computer playing the role of a DBMS server has a video monitor and keyboard in its configuration, these devices are not used in normal operation. The DBMS server computer interacts with user computers (and, accordingly, with users) through the network, and only through the network.
How is this approach better than the first?
Since a personal computer acts as a terminal, the user can perform additional data processing locally without loading the resources of the DBMS server. This can significantly improve system performance, especially with a large number of users.
If Windows is used as the workstation operating system, any user can format the results of a database query in the format word processor Microsoft Word for Windows or spreadsheet Microsoft Excel. The resulting document can then be formatted and printed on a laser printer (networked, of course!). This is impossible if all the user has at his disposal is an alphanumeric video monitor with a green image and a keyboard.
So the network personal computers will allow you to create a database with collective access in the office. It's hard to imagine how this can be done if you only have a few computers that are not connected to each other in any way.
File sharing
Despite the rapid decline in the cost of disk devices, you can never have too much memory. If several users need access to the same large files, there is no point in copying them to each user's disk. workstation. Yes, this is not always possible.
On a local network, you can allocate one or more computers for so-called file servers (Fig. 1.4). File server disks usually have large capacities (hundreds of MB or even tens of GB). At the same time, they are available to workstation users in the same way as their local disks.

Rice. 1.4. File server on local network
If you place files on the file server disk, all network users (or only some of them at the choice of the network administrator) will have access to these files.
Outwardly, it will look as if one or more new disks will appear on each workstation. These disks will be almost indistinguishable in their "behavior" from the local workstation disks, but they will be located on the file server (which is located, perhaps, in another room or even in another building).
As a memory device, you can connect a CD reader or a magneto-optical disk with data rewriting to the file server.
The cost of a CD reader is low, so it is usually installed at every workstation. However, the network allows you to organize shared access and save several hundred dollars.
At the same time, the cost of a magneto-optical recording device or a magnetic disk with a capacity of several GB is too high to equip all workstations with these “toys”. Therefore, if you need to organize the storage and collective use of a significant amount of data, a local network of computers will be a very good solution.
You can think of a file server as simply a shared disk device, and in most cases this won't be far from the truth.
One of the very useful uses of a file server is sharing files between different users. If there is no network, exchange is performed using floppy disks. Another option is to connect two computers via a serial port, but this option is slow and has other obvious disadvantages.
Now imagine that you need to copy a 100 MB file from your disk to the disks of other computers. You can calculate for yourself how many floppy disks and time this will require.
If all users have access to a shared disk device, you only need to copy the file to that device once. Then all other users will be able to access either the file you recorded on the disk of the file server, or they will be able to copy this file to their local disk.
Messaging and mail
While working, employees often exchange various information, including messages. In the days before computer networks, you could use two methods of transmitting messages.
The first method is that you yourself find the person you need and convey to him in words everything you need. Depending on how easy it is to catch a person at work, the process of transmitting a message can last a few minutes or several days.
The second method involves using a telephone or intercom. If the employee is on site, you give him a message. If not, ...however, you know all this very well yourself.
Local network allows you to organize transmission text messages between workstation users. All you need to do to send a message is select a user from the list, type the message text and click the universal "OK" button in the corresponding dialog panel. If the recipient's workstation is turned on, the message text appears on the screen, accompanied by a sound signal. Of course, if the employee is not there, all your efforts will be in vain.
The services provided by so-called e-mail are more convenient.
How does it work regular mail, you know well. You need to write a letter, seal it in an envelope, write the address (and also return address), and place the envelope in Mailbox. Everything further depends on the efficiency of postal employees.
Email works similarly. You compose the text of the letter and write it to a file. Then launch a special mail program, enter the recipient's address and the name of the file containing the prepared letter.
The mail program transmits the letter over the network to the recipient (naturally, you need to specify a special “electronic” address of the recipient, such as the name of a computer on the local network or a unique user identifier).
One of the network computers performs the role mail server. It receives letters, puts them in the mailboxes of recipient users, delivers these letters to the recipient “in hand” upon special request, and also distributes mail to other networks.
Without going into technical details of the organization yet Email, note that it allows you to transfer a file to the recipient, even if the latter is on vacation and relaxing at sea. When the recipient goes to work and turns on his computer, he will receive a message that mail has arrived in his name and can be picked up.
Since individual computers and local networks of computers can easily be connected by telephone lines, you can send email anywhere in the world.
You can also organize collective work with a fax modem, when any network user can send faxes over one telephone line. Although the fax modem itself is inexpensive, there is no point in equipping every computer with one, because the number of free telephone lines in your company may be small.
A network fax modem is accessible from any workstation, giving users the illusion of having a personal fax modem.
Video conferencing
Relatively recently, a new area of using local networks has appeared and is rapidly developing - video conferencing.
To organize a video conference, each computer is equipped with a video camera and an audio adapter. Special software provides image and sound transmission between workstations.
Computer video conferencing makes it easier to hold meetings, but so far this pleasure is not cheap.
1.2. How to connect a computer to a network
Now you know what connecting computers into a network gives. But there are two more important questions: how to perform such a merger and how much will it cost?
Since the first part of the book is intended for users, we will not go into technical details now, but will only describe the basic principles. The more in-depth information in Part 2 is intended for technical personnel and network administrators.
The methods of unification depend on what kind of network is being created - local or global.
The local network
Connecting a computer (workstation or server) to a local network is done using a special network adapter. A network adapter is usually purchased separately, although some computers have built-in network adapters.
There are countless models of network adapters produced by dozens of companies. In the second part of our book, we will provide specific recommendations for choosing a network adapter. For now we will only note that all network adapters can be divided into two groups according to the topology for which they are intended.
The simplest local network can have a bus (Fig. 1.5) or star (Fig. 1.6) topology.

Rice. 1.5. Bus topology
The bus topology involves the use of one cable up to several hundred meters long, into which network adapters of workstations are connected. The obvious disadvantage of this solution is that if the cable breaks, the entire network goes down.

Rice. 1.5. Star topology
A star topology involves connecting each computer with its own cable to a splitter, which is designed as a separate device and equipped with its own power supply.
If one of the cables is broken, it will not affect the operation of the entire network. In any case, the harm from the damage will be less than in the case of a bus topology.
More complex network topology options are also possible. For example, a network may consist of several segments with a bus topology and several star branches.
Local networks can be divided into two groups based on the type of network software used.
The first group is networks with dedicated file servers.
In such networks, one or more computers run a special network operating system, such as Novell NetWare or IBM Lan Manager. One of the main tasks of a network operating system is to make network resources available to users, mainly server disk devices and network printers.
In this group of networks, users interact with the file server, but not with each other. They can, for example, write a file to a file server disk, read a file written by another user, or print something on a network printer. And although it is theoretically possible to transfer data directly between workstations (bypassing the file server), in practice it is impossible to work in this mode.
The second group is peer-to-peer networks.
In peer-to-peer networks, there are no computers specifically dedicated to operating as a file server or print server. A user of any workstation can easily turn his computer into a server, providing access to its resources for other users. An example would be the network Microsoft Windows for Workgroups, which we will pay a lot of attention to in our book.
Peer-to-peer networks are convenient in cases where users intensively exchange data during work. However, data exchange should not be understood as just file exchange.
The user can write any object to the local Clipboard clipboard, and then make this object available to all network users. This is very convenient, since now you do not need to save the object in a file, transfer the file over the network and import it into those documents where you need to insert this image.
Thus, a peer-to-peer local network allows users to organize joint work on one project, providing the ability to directly transfer data in any of the Clipboard formats.
All of this may seem difficult to understand at first. Fortunately, there is no need for the user to know the topological details of the network, since the network software handles data transfers across the network in any direction and automatically takes into account the physical implementation details of the system.
It is enough for the user to know whether his computer is connected to the network, what network resources are available to him (file and mail servers, DBMS servers, network printers, etc.) and how to use them. You should ask your network administrator or the employee responsible for system performance about this. Every company has at least one such person, so they will definitely help you. We, in turn, will tell you what questions should be asked to the network administrator and what questions should not be asked.
As for the cost of the network adapter, it is low. Depending on the manufacturer, model and performance, the cost can vary from 20 to 200 dollars. As a rule, inexpensive network adapters with average performance are chosen for workstations, and high-speed and, accordingly, more expensive models are chosen for file servers and DBMS servers. In any case, the costs of network equipment are not too burdensome. Especially when you consider the opportunities that will be available to you after creating a network.
Global network
Have you ever traveled to the other side of town just to copy a file several tens of kilobytes in size? If you constantly perform this procedure, it's time to think about purchasing a modem and connecting to one of the global networks of computers.
Modems can be internal or external.
The first ones look like a regular adapter and are inserted into the computer case. Many models of notebook computers have built-in modems that can additionally receive and transmit faxes.
Modern external modems can also work with faxes. They are assembled in a separate small-sized case with a built-in power supply and are connected to the asynchronous serial adapter port using a special cable.
The cost of a modem ranges from one and a half hundred dollars to several thousand dollars, but in most cases you will be satisfied with inexpensive models that provide data transfer rates of about 28,800 bits per second and use modern data transfer protocols. Such modems cost from 250 to 500 dollars.
So, in order to physically connect your computer to the global network, you just need to buy a modem and connect it to a regular telephone line. But where and how to call?
There are many global networks in the world, among which the most famous are Internet, Compuserve, Sprint, Relcom, FIDONET and many others. Some of these networks cover only certain countries or regions, while others are spread throughout the world. However, almost all networks are connected to each other, so, for example, knowing our address in the GLASNET network, you can send us a letter from any other network.
If we consider the topology of a global network, we can assume that it has the form of a complex graph, the nodes of which contain computers.
There are computers on the global network that are specially designated to work as mail servers. Such computers are connected to several telephone lines (or similar channels) at once, for which several modems are used.
End users connect their computers to the global network, as we have already said, also using modems (Fig. 1.6).

Rice. 1.6. Global network of computers
Now about where to call.
First, you need to select the global network to which you want to connect and use a regular telephone to call the representative office of the company that maintains the corresponding network (the telephone numbers are known from advertising; since they are constantly changing, we will not list them).
Various criteria can be used to select a network.
You should know that global networks can be paid or free. The former provide a high level of service and guarantee fast delivery of correspondence, while the advantages of the latter are limited, as a rule, to the absence of the need to pay money.
You must choose the most suitable option for yourself. You should not think that connecting to all paid networks is very expensive. In Russia, for example, almost all commercial firms are connected to the Relcom network, although there are other paid networks that provide the same level of service for a lower fee.
If you cannot afford paid email, try connecting to the free FIDONET network. To do this, you need to call using a modem to any electronic bulletin board (BBS) and contact the system operator. The corresponding rules can be downloaded as text files from the same BBS.
The BBS system operator can connect you to their FIDONET node or recommend another node.
As for specific phones, we can recommend that you turn to advertising again. Some of the most well-known hardware and software companies have their own message boards that are used for maintenance or advertising purposes. The advertising materials of such companies indicate the telephone number of the electronic bulletin board. You need to call this phone using a modem and a special terminal program.
Integration of local and global networks
There is software that can integrate local and wide area networks. In this case, one of the computers on the local network is connected through a telephone router (containing several modems) to the global network.
All users of such a network can work with the global network by accessing modems installed on the telephone router. Thus, there is no need to connect each workstation via a modem to a separate telephone line.
1.3. Restricting access to network resources
Now you know that a local network provides various resources for shared use, such as network printers, disk memory connected to file servers, mail servers, and so on.
When there are only a few users on a network, they often all have equal access to network resources. For example, any user can print to a network printer, send a fax, or write data to the disks of a file server.
However, in large companies, several groups of users with different “range of interests” may operate on the network. In this case, the administration may want to limit the access of certain users (or groups of users) to certain resources. Moreover, the disks of a file server or DBMS server may contain confidential information that should not be accessible to everyone.
Network operating systems have their own means of access control, more or less powerful.
Peer-to-peer operating systems, such as Microsoft Windows for Workgroups contain only the simplest tools. The user can allow or deny other users access to their local disk or printer, provide read and write access upon presentation of a password (different passwords can be used to allow read and write access).
In most cases, with a small number of users, such simple means of access control are sufficient. If there are increased requirements for data protection, a more complex network operating system such as Novell NetWare version 3.12 should be used for the file server.
In the latter case, the network administrator can organize access control to the file server disks at the directory and file level. Let's talk about this in more detail.
All users are united by the administrator into groups, and any user can be a member of several groups (or may not be a member of any of them).
For each group, the network administrator sets access rights to directories and files. A group can be assigned individual rights to read, to view the contents of directories, to write, to delete, and the right to change rights for other groups and users.
If a user group has any rights to access files and directories, all users in that group also have these rights. However, the network administrator can assign some users individual rights that are greater or lesser than the rights of the group to which the user belongs.
It is noteworthy that if a Novell NetWare user does not have rights to view the contents of a directory, then under no circumstances will he see which directories and files are located in the “forbidden” directories for him. The principle here is that what you don’t know won’t hurt you. Therefore, if the user does not have any rights in the directory, he simply will not know that such a directory exists on the disks of the file server (a convenient way to hide the GAMES directory from management, isn’t it?).
Similarly, you can organize access to a network printer.
As for restricting access to information stored in the DBMS, it is best to use tools specifically designed for this purpose that are included in the DBMS.
Note that users usually do not “see” the disks of the DBMS server in the same way as they see the disks of the file server. And, therefore, they cannot copy data files to their local drives with the secret thought of reading information that is forbidden to them. Data is accessed using special requests to the DBMS server, and the DBMS server itself decides what data can be sent specific user, and which ones are not.
In that brief overview We have only touched upon the main points of protective equipment; more detailed information is yet to come.
Local area network (LAN) is a complex of equipment and software, providing transmission, storage and processing of information.
Purpose of local networks
The purpose of a local network is to provide shared access to data, programs and equipment. A team of people working on one project has the opportunity to work with the same data and programs not in turn, but simultaneously. A local network provides the opportunity to share equipment. The best option is to create a local network with one printer for each department or several departments. File server The network allows for shared access to programs and data.
The local network also has an administrative function. Monitoring the progress of projects online is easier than dealing with multiple offline computers.
The local network (LAN) includes the following equipment:
- Active equipment – switches, routers, media convectors
- Passive equipment – cables, mounting cabinets, cable channels, patch panels, information sockets
- Computer and peripheral equipment – servers, workstations, printers, scanners.
Depending on the requirements for the designed network, the equipment used during installation may vary.
Basic characteristics of a local network
Currently, in different countries of the world, various types of LANs with different sizes, topology, operating algorithms, architectural and structural organization have been created and are in operation. Regardless of the type of network, they are subject to general requirements:
- Speed is the most important characteristic of a local network
- Adaptability - the ability of a local network to expand and install workstations where required
- Reliability is the property of a local network to maintain full or partial functionality, regardless of the failure of some nodes or end equipment.
Local network topology
The topology (layout, configuration, structure) of a computer network usually refers to the physical location of computers on the network relative to each other and the way they are connected by communication lines. It is important to note that the concept of topology refers primarily to local networks, in which the structure of connections can be easily traced. In global networks, the structure of connections is usually hidden from users and is not very important, since each communication session can be carried out along its own path.
The topology determines the requirements for equipment, the type of cable used, the permissible and most convenient methods of managing the exchange, reliability of operation, and possibilities for network expansion. And although a network user rarely has to choose a topology, it is necessary to know about the features of the main topologies, their advantages and disadvantages.
There are three basic network topologies:
- Bus (bus) - all computers are connected in parallel to one communication line. Information from each computer is simultaneously transmitted to all other computers
Star (star) - comes in two main types:
- Active star (true star) - one central computer is connected to other peripheral computers, each of them using a separate communication line. Information from a peripheral computer is transmitted only to the central computer, from the central one - to one or more peripheral
- A passive star that only looks like a star (Fig. 2). Currently, it is much more widespread than an active star. Suffice it to say that it is used in the most popular Ethernet network today
In the center of a network with this topology, there is not a computer, but a special device - a switch or, as it is also called, a switch (What is a Switch?), which restores incoming signals and sends them directly to the recipient.
Ring - computers are sequentially combined into a ring.
The transmission of information in the ring is always carried out in only one direction. Each computer transmits information only to one computer next in the chain behind it, and receives information only from the previous computer in the chain.
In practice, other local network topologies are often used, but most networks are focused on three basic topologies.
Local area network (LAN, local network / Local Area Network, LAN) - a computer network that provides data transfer to short distances with a speed, as a rule, of at least 1 Mbit/s. The characteristic features of the LAN are:
1. Territorial coverage - from several tens of meters to several kilometers.
2. Typically connects personal computers and other electronic office equipment, allowing users to exchange information and efficiently share shared resources such as printers, modems, and storage devices.
3. Interface - serial.
4. There is no ADF, since the signals are transmitted in “natural” digital form.
5. A fairly simple device is used as a device to interface the computer with the transmission medium - a network adapter.
6. Simple typical topologies: “common bus”, “ring”, “star”.
7. There is no routing (layer 3 of the OSI model).
8. High data transfer speed, usually more than 1 Mbit/s.
9. Relatively low costs for building a network.
The listed features determine the main advantages
LAN, consisting in the simplicity of network equipment and organization cable system and, as a result, the ease of operation of the network.
In general, a LAN includes:
Many computers, usually personal computers (PCs), called workstations;
Network adapters, which are an electronic board for connecting a PC with communication means;
The transmission medium (backbone), which is a set of communication means (communication network, communication network), uniting all PCs into a single computer network cable system or radio communication.
Network adapters (NA) (boards, cards) are designed to interface a PC with communication means, taking into account the rules of information exchange accepted in a given network.
The list of functions assigned to the CA depends on the specific network and, in general, can be divided into two groups:
1) trunk (channel) functions that ensure pairing of the adapter with a PC and the network backbone;
2) network functions that ensure data transmission in the network and implement the exchange protocol adopted in the network.
The main functions of the SA include:
1) electrical buffering of highway signals;
2) recognition (decryption) of one’s own address on the highway;
3) processing of exchange strobes on the highway and generation of internal control signals.
CA network functions include:
1) galvanic isolation of the PC and communication means (absent in the case of fiber optic and wireless communication);
2) conversion of signal levels when transmitting and receiving data;
3) encoding of signals during transmission and decoding during reception (absent when using the NRZ code);
4) recognition of your frame upon reception;
5) code conversion: parallel to serial when transmitting and serial to parallel when receiving;
6) buffering of transmitted and received data in buffer memory SA;
7) conducting arbitration of exchanges over the network (monitoring the state of the network, resolving conflicts, etc.);
8) calculation of the frame checksum during transmission and reception.
The first four functions are always implemented in hardware, the rest can be implemented in software, which naturally reduces the exchange speed.
The following topologies are most widely used in LANs.
1. “Bus” (bus) - is a cable called a trunk or segment to which all computers on the network are connected (Fig. 72).
A frame transmitted from any computer is distributed along the bus in both directions and enters the buffers of the network adapters of all computers on the network. But only the computer to which this frame is addressed stores it in a buffer for further processing. Please note that only one computer can transmit at a time.
The following factors affect network performance (data transfer speed):
The number of computers on the network and their technical parameters;
Intensity (frequency) of data transmission;
Types of running network applications;
Type network cable;
The distance between computers on the network.
To prevent the reflection of electrical signals, terminators are installed at each end of the cable to absorb the reflected signals.
If the integrity of the network is violated (cable break or disconnection), as well as in the absence of terminators, the network “falls” and stops functioning.
2. “Star” (star), in which all computers are connected to a central component - a hub (Fig. 73).
The transmitted frame can be available to all computers on the network, as in the “bus” topology, or, in the case of a smart hub operating at layer 2 of the OSI model, it can be sent to a specific computer in accordance with the destination address.
The main disadvantages of this topology are:
Significant cable consumption for geographically large networks;
Low reliability (bottleneck - hub).
3. "Ring" (ring). Signals are transmitted along the ring in one direction and pass through each computer (Fig. 74). Unlike a passive bus topology, each computer acts as a repeater, writing frames to the network adapter buffer and then passing them on to the next computer.
Rice. 73 
Depending on the method of signal transmission, there are:
Rice. 74 
1) passive topologies, in which computers only “listen” to data transmitted over the network, but do not move it from the sender to the recipient, so the failure of one of the computers does not affect the operation of the others;
2) active topologies in which computers regenerate signals and transmit them over the network.
3.2 LAN architectures
The following LAN architectures are distinguished:
Peer-to-peer networks;
Client-server networks;
Combined networks in which both types can operate operating systems(peer-to-peer and server-based).
Peer-to-peer networks are networks with equal computers that can use each other's resources.
Some peer-to-peer networks allow you to use computers both as a workstation within the network and as a dedicated or non-dedicated server.
A peer-to-peer network architecture is justified if:
The number of users does not exceed 10;
Users are located compactly;
Data protection issues are not critical;
There is a need to increase the productivity and efficiency of office activities by sharing files and peripheral equipment.
Advantages:
Moderate cost;
Easy to build and operate (no need for network administration).
Flaws:
Small size a network that usually unites no more than 10 users (computers) forming working group;
It is difficult to ensure proper protection of information when large size networks.
Examples of peer-to-peer network operating systems are LANtastic (from Artisoft), NetWare Lite (Novell). Peer-to-peer support is also built into operating systems. Windows systems(Windows NT Workstation, Windows 95, etc.) from Microsoft.
Client-server networks contain:
Servers - powerful computers, owning resources shared between network users and managing clients’ access to them;
Clients are less powerful computers on the network that own unshared resources and have access to server resources.
A client-server network architecture is justified if:
The network plans to work with a single network resource, for example, simultaneous work of several users with a common database located on a server;
It is advisable to concentrate all shared network resources (for example, a network printer) in one place and does not require communication between workstations.
Advantages:
High performance due to sharing of network resources;
Possibility of organizing effective data protection;
Effective organization Reserve copy data;
Ability to support hundreds and thousands of users online;
Good opportunities for expansion.
Flaws:
They require constant qualified administration services.
LAN server is a dedicated computer that provides other computers on the network with access to shared network resources. A program that responds to and executes appropriate requests is called a service.
Servers are divided into:
File servers;
Application servers.
The file server provides access to the shared disk space where publicly accessible files are stored and basically defines the capabilities of the LAN.
Application servers are a means of expanding the capabilities of a LAN and include: a database server, a print server, a backup server, a fax server, etc.
3.3 Multi-segment LAN organization
The main disadvantage of a LAN is the presence of restrictions on the total length of the cable network, which is several hundred meters.
So for the Ethemet standard, the length of the segment (the distance from one extreme station to the other) is no more than 500 meters - for an electrical cable.
The maximum distance between the two most distant (outermost) stations is called the network diameter.
The simplest way to increase the network diameter and the number of computers is a multi-segment LAN organization using:
Several network adapters in a file server;
Repeaters;
Concentrators.
One of the first and simplest solutions aimed at increasing the size of a local network was the use of several network adapters (Fig. 75), which made it possible to almost double the network diameter compared to a single-segment LAN.
Rice. 75 
For example, the Ethemet network could have up to 5 segments, each with a separate cabling system.
Dignity:
Ease of implementation and low cost.
Flaws:
The need to use an additional network adapter (NA) for each segment;
Heavy load on the server and, as a result, the impossibility of building large (with a large number of workstations) networks.
A repeater is the simplest network device for building multi-segment LANs, amplifying the signal received from one segment and transmitting it to another segment (Fig. 76).
Rice. 76 
A repeater takes signals from one cable segment and repeats them bit by bit synchronously in another segment, improving the shape and power of the pulses, and synchronizing the pulses.
The repeater unites absolutely identical networks and operates at the lowest - physical level of the OSI model.
Advantages:
Ease of organization of multi-segment LANs;
Cheapness.
Flaws:
Significant increase in load in both segments, because even "local" messages from one segment are transmitted to another network;
Reduced performance (data transfer speed) of the data transmission system.
A hub (hub) is a network device used in twisted-pair networks, in which cable sections coming from workstations are concentrated (Fig. 77, a).
Rice. 77 
Through a hub, the computer is connected to a single medium for data exchange between LAN stations - a server or a backbone channel. The simplest hub is a multiport repeater and is used as the central node of a LAN with a “Star” topology. The hub can have from 8 to 32 ports for connecting computers. A further increase in the number of ports is achieved by combining hubs into a single stack of hubs, as shown in Fig. 77, b.
In addition to ports for connecting workstations using twisted pair, hubs can have a connector for connecting to a high-speed backbone on a coaxial cable or fiber optic cable.
3.4 LAN access control methods
The efficiency of the LAN is significantly influenced by the Access Control Method, which determines the procedure for providing network nodes with access to the data transmission medium in order to provide each user with an acceptable level of service. Methods for accessing the transmission medium are implemented at the data link layer of the OSI model.
The classification of access methods is presented in Fig. 78.
Rice. 78 
Multiple access is a method of access of multiple network nodes to a common transmission medium (for example, a common bus), based on stations competing for access to the transmission medium. Each station may attempt to transmit data at any given time.
Multiple access methods include:
Random access;
Timed access;
Carrier sense access with collision detection;
Carrier sensing and collision avoidance access.
The simplest and most natural method of accessing a common transmission medium is random access, which means that each network station begins transmitting a frame at the moment it appears (formed), regardless of whether the common transmission medium is busy or free. If two or more stations transmit at the same time, their frames are mutually distorted and a collision occurs. Fig. 79, a) shows the case when two workstations PC1 and PC2 begin transmitting frames “Frame 1” and “Frame2” at random times t1 and t2, respectively. At moment t2, a collision occurs (Fig. 79, b), distorting both frames. The utilization rate of the communication channel with the random access method is approximately 16%.
Reducing collisions and increasing the utilization rate of the communication channel can be achieved through the use of clocked access, which consists of the following. The entire time interval is divided into cycles of length T, where the value of T must be greater than the transmission time of a frame of maximum length. Each workstation can begin transmitting a frame only at the beginning of the next clock cycle. In this case, “Frame2” will be transmitted in a different clock cycle in relation to “Frame1” (Fig. 79, c), and a collision will not occur. However, it should be noted that the probability of collisions remains quite high in cases where the moments of frame formation in different stations are within the same clock cycle. In this regard, the utilization rate of the communication channel, although increasing, is insignificant, and amounts to approximately 32%.
Rice. 79 
Carrier Sense Multiple Access with Collision Detection (CSMA/CD) is a medium access method in which a station having data to transmit listens to the channel to determine if it is transmitting data at that time. another station. The absence of a carrier signal means that the channel is clear and the station can begin transmitting. However, it is possible that during the time the signal propagates through the transmission medium, other stations will also begin transmitting their data almost simultaneously.
During transmission, the station continues to listen to the channel to ensure there is no collision. If a collision is not detected, the data is considered successfully transmitted.
If a collision is detected, the station repeats the transmission after some random time. Retransmissions are repeated until the data is successfully transmitted.
Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is a method of accessing the transmission medium in which data transmission is preceded by sending a blocking signal (jam) in order to seize the transmission medium for exclusive use. This access method is recommended for wireless LANs.
Token access presupposes the presence in the network of a frame of a special format, called a token, which continuously circulates in the network and controls the process of access of workstations to the data transmission medium. At any given time, only the station that owns the token can transmit data. The workstation that owns the token attaches its data frame to the token and sends it to the recipient. In this case, various options are possible for releasing and transferring the token to another station:
1) release of the token by the addressee: the addressee detaches the token from the data and can use it to send its frame, if any, or transfer the token to another station;
2) release of the token by the sender: the token with the attached data frame makes a full rotation and is released by the sender (in the Token Ring version for 4 Mbps speed) if it was returned without errors; otherwise, the same frame with the marker is re-sent to the data transmission medium;
3) method of early release of the ETR token (Eagly Token Release), when the workstation releases the token immediately after transmitting its data and transmits it to another station without waiting for the return of the sent data frame (in the Token Ring version for 16 Mbit/s speed and in the FDDI network ).
Token access is used in networks:
With a bus topology in the ARCnet LAN (Token B us - token bus);
With a ring topology in the LAN Token Ring and FDDI (Token Ring).
3.5 LAN Ethernet
Ethernet is a LAN technology developed jointly by DEC, Intel and Xerox (DIX) in 1980 in the form of the Ethernet II standard for a 10 Mbit/s network built on coaxial cable.
Depending on the physical data transmission medium, various options for implementing a LAN at the physical level are provided:
L0Base-5 - thick coaxial cable;
L0Base-2 - thin coaxial cable;
L0Base-T - twisted pair;
L0Base-F - fiber optic.
Other Ethernet LAN options and the years of appearance of the corresponding standards are presented in Table 3.1.

The IEEE 802.3 standard defines the access method used in Ethernet networks (including Fast Ethernet and Gigabit Ethernet) CSMA/CD - carrier sense multiple access and collision checking.
For all variants of the physical layer of Ethernet technology providing a throughput of 10 Mbit/s, Manchester encoding is used.
10Base-5 is a physical layer standard that describes the operation of an Ethernet network on a thick coaxial cable (thick Ethernet) used as the main backbone.
Figure 80 shows an Ethernet LAN segment on a thick coaxial cable.
Workstations are connected to the main cable using a transceiver cable consisting of 4 twisted pairs up to 50 m long and a transceiver located directly on the coaxial cable. A transceiver is an electrical device that physically transmits and receives data. The distance between adjacent transceivers must be a multiple of 2.5 m to eliminate the influence of standing waves in the cable on the quality of signal transmission. Terminators are located at the ends of the main cable, absorbing the information signal propagating in the cable and preventing the occurrence of a reflected signal that distorts the useful signal.
Rice. 80 
Despite the bulkiness and difficulties during wiring, such a cable system allows you to build fairly extensive networks.
The main limitations for a single Ethernet LAN segment according to the 10Base-5 specification are as follows:
Maximum segment length (distance between extreme nodes) - 500 m;
The minimum distance between transceivers is 2.5 m;
The maximum number of nodes (transceivers) on a segment is 100;
The maximum length of the transceiver cable is 50 m.
The 10Base-5 standard allows for the construction of multi-segment networks using repeaters. The maximum number of segments in the network allowed by the standard is 5. This limitation is due to the fact that repeaters only amplify the signals without restoring their shape, which, with a large number of segments in the network, can lead to a significant percentage of errors.
10Base-2 is a physical layer standard that describes the operation of an Ethernet network on a thin coaxial cable (thin Ethernet).
The stations are connected directly to the main line through T-shaped BNC connectors (Fig. 81).
Rice. 81 
A thin coaxial cable runs through the network adapters of all stations. Otherwise, the principles and rules for constructing single- and multi-segment LANs on thin and thick coaxial cable are similar. The only difference is the restrictions on the size of the network and the number of stations.
The main limitations for an Ethernet LAN according to the 10Base-2 specification are as follows:
Maximum segment length (distance between extreme nodes) - 185 m;
The maximum number of nodes on a segment is 30;
The minimum distance between nodes is 1 m;
A multi-segment network is built according to the “5-4-3” rule: a maximum of 5 segments, 4 repeaters, and 3 segments are loaded;
In each of the three (middle and two extreme) segments, up to 30 nodes can be connected to the cable;
The other two segments are used only to increase the total length of the network; stations cannot be connected to them;
A repeater is treated as a special node connected to the network, so a network with two repeaters is only allowed to have 28 stations.
The 10Base-T specification describes an Ethernet network with a star topology and a cabling system based on unshielded twisted pair According to the 10Base-T specification, a network segment is the cable connecting the workstation and the hub. This means that only two devices can be connected to each segment: a station and a hub (Fig. 82), and the number of segments is equal to the number of stations connected to the hub.
For simplicity of reasoning, by a 10 Base-T Ethernet network segment we mean a hub with all the stations connected to it. A multi-segment network will be a combination of several hubs with stations connected to them (Fig. 82).
Rice. 82 
When building a multi-segment Ethernet 10 Base-T network, the “4 hubs” rule is used, which states that between any two stations in the network there should be no more than 4 concentrators (hubs).
The main restrictions for an Ethernet LAN in accordance with the 10Base-T specification are as follows:
Maximum cable length (between a hub and a workstation or between two hubs) is 100 m;
The number of concentrators between any stations is no more than 4;
Maximum network diameter - 500 m;
The maximum number of stations in the network is 1024 (can only be achieved through the use of 32 port hubs (Fig. 8 3).
Thanks to the lower cost of the cable system and the ability to build networks with the maximum number of stations, 10Base-T networks have gained a dominant position in the market and have almost completely replaced networks built on coaxial cable.
10Base-F is a set of physical layer standards that describe the operation of an Ethernet network on a fiber-optic cable with a bandwidth of 10 Mbit/s. Multimode fiber optic cable (FOC) is used as a data transmission medium in a fiber-optic Ethernet network.
Rice. 83 
The structural organization of the network is similar to the 10 Base-T standard: network adapters of workstations are connected to a multiport repeater (hub) using a fiber optic cable and form a physical “Star” topology.
10 Base-F includes the following standards.
1. FOIRL standard (Fiber Optic Inter-Repeater Link): the length of the fiber optic cable between nodes or repeaters is up to 1 km; maximum number of repeaters 4; maximum network diameter is 2500 m.
2. The 10Base-FL (Fiber Link) standard is an improved version of the FOIRL standard, which consists in increasing the transmitter power, due to which the maximum distance between the node and the repeater can reach 2000 m, while: the maximum number of repeaters 4; maximum network diameter is 2500 m.
3. The 10Base-FB (Fiber Backbone) standard is intended only for combining repeaters into a backbone, while: up to 5 10Base-FB standard repeaters can be installed between network nodes; maximum length of one segment - 2000 m; maximum network diameter is 2740 m.
Unlike previously discussed networks, the repeaters used in the Ethern et 10 Base-FB LAN, when there are no frames to transmit, exchange special sequences of signals, which allows you to constantly maintain synchronization in the network. Therefore, a LAN built according to the 10Base-FB standard is called “synchronous Ethernet”. Due to lower delays when transferring data from one segment to another, the number of repeaters has been increased to 5.
The advantages of an Ethernet LAN include:
Easy to install and operate;
Low cost of implementation due to the simplicity and low cost of network adapters and hubs;
Possibility of use various types cables and cable system laying diagrams.
The disadvantages of the Ethernet network include:
Reducing the actual data transfer speed in a heavily loaded network, up to its complete stop;
Difficulties in troubleshooting: when a cable breaks, the entire LAN segment fails and it is quite difficult to localize the faulty node or section of the network.
Computer networks are designed for common use And public access to various network services. When determining the size of computer networks, it is customary to distinguish between local networks Local Area Networks (LAN) and Wide Area Networks (WAN). Local networks are used on the scale of one organization or its divisions, since they cover a small area, no more than 2 km. The advantage of such networks is that they use high-quality communication lines, and information exchange occurs at high speed.
Global networks are computer networks located over a wide area, for example in cities or even countries. Such networks are characterized by the use of standard communication channels (for example, telegraph, telephone, satellite channels). The information transmission speed of such communication lines is low, only a few kilobits per second. WAN services are limited - they transfer files, usually in the background and using email. When transferring data, methods and equipment different from local networks are used, as well as the process of monitoring and restoring information, since the transfer occurs with significant distortions.
In local networks, various communication channels pass jointly through several network nodes; in global networks they are used separately. Local networks are characterized by uneven load distribution. There is so-called bursty traffic, when the load increases 100 times. Therefore, to connect nodes in local networks, the packet switching method is used, which is more efficient than the traditional one. Global networks are characterized by the use of not only circuit switching methods, but also circuit switching methods and the use of non-switched circuits.
Local networks are characterized by poor scalability due to certain settings of the basic topologies, which determine the method of connection to the station and the length of the line. WANs are highly scalable because they were designed to accommodate arbitrary topologies.
As a result of the development of new technologies and the installation of the latest equipment, the speed of information transfer in global networks becomes the same as in local ones, for example, in global ATM networks - 622 Mbit/s. Also, the on-line mode is already characteristic of global networks (for example, for the WWW information service, which uses hypertext and provides information on the Internet).
Local networks borrowed transport technologies from global ones. New high-speed technologies are emerging, for example Gigabit Ethernet, Fast Ethernet, operating on individual lines along with conventional shared lines.
Local networks 1. A computer network is: 1) a group of computers located in the same room; 2) combining several computers to jointly solve problems; 3) a set of terminals connected by communication channels to a large computer; 4) multimedia computer with printer, modem and fax. 2. Network technologies - this is: 1) the main characteristic of computer networks; 2) forms of information storage; 3) technologies for processing information in computer networks; 4) a method of connecting computers on a network. 3. Information systems are: 1) computer networks; 2) information storage; 3) systems that control the operation of the computer; 4) systems for storing, processing and transmitting information in a specially organized form. 4. A local network is: 1) a group of computers in one building; 2) a complex of connected computers for joint problem solving; 3) low-current communications; 4) ShereE system 5. What is not typical for a local network: 1) high speed of information transfer; 2) the ability to exchange information over long distances; 3) the presence of a connection for all subscribers of a high-speed channel for transmitting information in digital form; 4) availability of a channel for transmitting information in graphical form? 6. What communication lines are used to build local networks: 1) twisted pair only; 2) fiber optic only; 3) only thick and thin coaxial cable; 4) twisted pair, coaxial cable, optical fiber and wireless communication lines? 7. The network adapter performs the following functions: 1) implements one or another access strategy from one computer to another; 2) encodes information; 3) distributes information; 4) converts information from numerical form to text form, and vice versa. 8. Types of network adapters: 1) Arcnet, Internet; 2) SoundBlaster, Token Ring; 3) Ethernet, hard drive; 4) Arcnet, Token Ring, Ethernet. 9. A server is: 1) one or more powerful computers for servicing the network; 2) high-performance computer; 3) keeper of the bootstrap program; 4) multimedia computer with modem. 10. The main function of the server: 1) performs specific actions based on client requests; 2) encodes information provided by the client; 3) stores information; 4) sends information from client to client. 11. For data transmission in the network, the following basic schemes are used: 1) competitive and logical; 2) competitive and with lexical access; 3) competitive with token access; 4) with marker access and with lexical access? 12. What scheme does the Ethernet network use to transmit data over the network: 1) with token access; 2) competitive scheme; 3) logical circuit; 4) with lexical access. 13. The Token Ring network uses the following scheme: 1) logical; 2) competitive; 3) with token access; 4) with lexical access? 14. According to what scheme is data transferred in the Arcnet network: 1) logical; 2) with lexical access; 3) with token access; 4) competitive? 15. What are the configurations (topologies) of a LAN: 1) tree-like, simply connected, fully connected, parallel; 2) bus, simply connected, star-shaped, fully connected; 3) ring, bus, star, fully connected and tree; 4) tree-like, multi-connected, few-ringed, sequential? 16. What methods of access from computer to computer are used in the LAN: 1) marker method, direct access; 2) time reservation method, coding method; 3) direct access, coding method; 4) marker method, time reservation method? 17. Components involved in data transmission over a network: 1) source computer, transmitter, cable network, receiver; 2) source computer, cable network, receiver and destination computer; 3) file server, puncture unit, cable network, destination computer; 4) source computer, protocol unit, transmitter, cable network, receiver and destination computer. 18. A protocol is: 1) a data packet; 2) rules for organizing data transmission in the network; 3) rules for storing data on the network; 4) structuring of data on the network. 19. Specific functions of drugs for educational purposes: 1) support file system, data protection and access control; 2) system of control and lesson management; 3) definition working system, data decoding, control system; 4) data delimitation, data protection, access system, definition of a working system, access delimitation, control and lesson management system. Operating systems of local networks 1. What is the purpose of operating systems of local networks: 1) training functions; 2) application program for client; 3) provides sharing network hardware resources and the use of distributed collective technologies when performing work; 4) a special LAN component for setting up data transfer using a given protocol? 2. NetWare OS is: 1) a network OS with centralized management; 2) network OS with a democratic control principle; 3) hierarchical OS for peer-to-peer and multi-rank systems; 4) specific OS for communication with the Internet. 3. What is used when starting NetWare OS: 1) text file; 2) core - file server.exe; 3) nlm module; 4) system volume SYS? 4. What is the purpose of the syscon.exe utility: 1) storage of individual subdirectories of network users; 2) with its help, the system administrator performs all the work of limiting user access; 3) creates a separate subdirectory for each network user; 4) does it contain a program for connecting the user to the network? 5. NetWare file system capabilities: 1) provides transparent access to file server disk partitions; 2) supports an extensive system for restricting access to files and directories of the file server from various workstations; 3) creates a system volume SYS; 4) divides network users into groups. 6. Which directory contains network programs and utilities for the user in NetWare: 1) SYSTEM; 2) USERS; 3) MAIL; 4) PUBLIC? 7. What is the purpose of the LOGIN command (NetWare OS): 1) the user connects to the file server; 2) maps the file server directories to the local disks of the workstation; 3) disconnects from the file server; 4) allows you to get detailed information about files? 8. Which command disconnects from the file server (NetWare OS): 1) map; 2) Login; 3) Logout; 4) ndir? 9. What is the salvage dialog utility (NetWare OS) intended for: 1) to manage the server; 2) allows you to send short messages from one workstation to another; 3) to restore by chance deleted files; 4) to view information about a user group? 10. Which utility is designed to manage the server (NetWare OS): 1) session; 2) syscon; 3) send; 4) filer? Global networks 1. In global networks there are two modes of information exchange - these are: 1) user and network; 2) informed and hidden; 3) interactive and user; 4) interactive and batch. 2. On-line is: 1) an information network; 2) team; 3) real time mode; 4) utility. ^ 3. The largest Russian telecommunications network: 1) BITNET; 2) APRANET; 3) NET; 4) RELCOM. 4. OMine is: 1) information packet exchange mode; 2) team; 3) telecommunications network; 4) operating system. 5. Worldwide teleconferencing system: 1) Eunet; 2.Fidonet; 3. Relcom; 4. Usenet. 6. BBS is: 1) a computer network; 2) teleconference system; 3) electronic bulletin board; 4) operating mode. 7. BBS is intended: 1) to determine the route of information; 2) for exchanging files between users; 3) to view addresses; 4) for information management. 8. The host machine is: 1) an information bank; 2) computer communication centers; 3) multimedia computer; 4) information storage machine. 9. A modem is: 1) a conversion device digital signals to analog and vice versa; 2) transport basis of the network; 3) information storage; 4) a device that controls the process of information transfer. 10. Modem functions: 1) connects the computer to the nearest node; 2) serves as a network card for connecting computers to a local network; 3) carries out logging of transmitting information; 4) protects information. 11. The transport basis of global networks is: 1) twisted pair; 2) coaxial cable; 3) telephone lines and satellite channels; 4) telegraph. 12. To communicate between computers via modems, the following are used: 1) only telephone lines; 2) only satellite channels; 3) radio waves only; 4) telephone lines, optical fiber, satellite channels and radio waves. 13. Based on the method of communication, the following data transmission modes are distinguished: 1) full-duplex and half-duplex; 2) simultaneous and phased; 3) high-speed and simultaneous; 4) duplex and simultaneous. 14. According to the method of data grouping, modes are distinguished: 1) single-digit and single-block transmission; 2) polysyllabic and monosyllabic transmission; 3) serial and parallel; 4) synchronous and asynchronous. 15. What are MNP modems: 1) modems with hardware compression and information correction; 2) modems with information encoding; 3) modems with information security; 4) modems modified in speed? 16. What is more important for organizing a network: 1) availability large quantity computers; 2) protocol system; 3) several network operating systems; 4) high-speed modems? 17. What do network layer protocols provide: 1) provide network data transfer modes; 2) access to network resources; 3) connect different networks; 4) are they testing the network? 18. Transport protocols perform the following functions: 1) group messages; 2) encode information packets; 3) are responsible for the exchange between host machines; 4) control the input and output of data. 19. What application protocols are responsible for: 1) for data transfer and access to network resources; 2) form data packets; 3) control the operation of host machines; 4) test the correct operation of the network? 20. A router (router) is: 1) powerful computers connecting networks or sections of a network; 2) track the path from node to node; 3) determine network addressees; 4) program for routing data packets. 21. The technical structure of E-mail is: 1) a set of hub stations communicating with each other for exchange; 2) a set of computers on the local network; 3) computers that store and encode information; 4) computers sending information upon requests. 22. A typical email subscriber station consists of: 1) several network computers; 2) from a computer, special program and modem; 3) from a computer and mail server; 4) from host machines. 23. Typical structure of an email: 1) title, subject of the message, full name of the addressee; 2) title, subject of the message, type of letter, sender's address; 3) date of departure, address, return address, message subject and text; 4) message subject, The address book, text and title. 24. A domain is: 1) the name of a file in a mailbox; 2) mailbox of the hub station; 3) country code; 4) short name of the recipient. 25. What is the protocol basis of the Internet: 1) the system of IP addresses; 2) testing protocols network computer; 3) sequence of addresses; 4) address book? 26. What does an 1P address consist of: 1) network addresses; 2) sequences of addresses; 3) protocols; 4) network addresses and host numbers? 27. What protocol does the Internet support: 1) SCP/IP; 2) SCP; 3) TCP/IP; 4) QCP/IP? 28. The main components of IP technology: 1) identification, length of the IP header; 2) IP packet format, IP address, IP packet routing method; 3) ASCII format and IP address format; 4) IP packet format, method of communication on English language. 29. What the DNS server program provides: 1) information encoding; 2) search for numeric addresses; 3) establishes a correspondence between domain names and IP addresses; 4) searches for IP addresses? 30. What are Ping programs used for: 1) to trace packets; 2) to check the passage of IP packets; 3) to identify packet damage during transmission; 4) to determine the IP address? 31. To support E-mail on the Internet, the following protocol has been developed: 1) STTP; 2) SMTP; 3) SCTP; 4) SSTP. 32. What encoding standard is used on the Internet: 1) UUCD; 2) MIME; 3) RFC-822; 4) WHOIS? 33. Letter coding is used: 1) to speed up the transfer of information; 2) for the transfer of classified information; 3) for transferring binary files and some text files; 4) historical “rules of the game” of email. 34. FTP archive is: 1) Archie server; 2) file storage; 3) database; 4) WEB site. 35. Initial command for a session with the FTP server: 1) close; 2) get; 3) open; 4) ftp. 36. User registration FTP server: 1) ftp; 2) cd; 3) is; 4) user. 37. cd command FTP protocol used: 1) to change the current directory; 2) for user registration; 3) to navigate through the file system tree; 4) to start the session. 38. Which command should be used to view FTP directories: 1) Is; 2) mget; 3) bin; 4) get? . 39. Which FTP command can be used to receive or transfer one file: 1) get, put; 2) mget, mput; 3) bin; 4) Is, cd? 40. To receive/transmit dialing FTP files The command used is: 1) get, put; 2) ls, cd; 3) user; 4) mget, mput. 41. WWW is: 1) distributed Information system hypertext-based multimedia; 2) eBook; 3) protocol for posting information on the Internet; 4) file sharing information environment. 42. Hypertext is: 1) an information shell; 2) text containing illustrations; 3) information in the form of documents with links to other documents; 4) information storage. 43. Client-server interaction when working on the WWW occurs using the following protocol: 1) HTTP; 2) URL; 3) Location; 4) Uniform. 44. Which programs are not WWW browsers: 1) Mosaic; 2) Microsoft Internet Explorer; 3) Microsoft Outlook Express; 4) Netscape Navigator? 45. HTML is: 1) a program for viewing WWW documents; 2) application program; 3) hypertext markup language; 4) client-server interaction protocol. 46. In HTML you can use: 1) text in ASCII format; 2) text of any format and graphic drawings; 3) any multimedia files; 4) any data types. 47. What are symbols used for in HTML: 1) to highlight a paragraph; 2) to highlight a paragraph, point; 3) to highlight chapters; 4) to highlight the title? 48. What characters in HTML separate the main text from the accompanying text: 1) ; 2) ; 3) ; 4) ? 49. How a link to another document is described in HTML: 1); 2) indicating their URL; 3) ; 4) ? 50. How links to documents stored on other servers are written in HTML: 1) indicating their URL; 2) ; 3) ; 4) ? 51. How to set the position of a picture in HTML: , 1) ; 2) ; 3) ; 4) ? 52. What is the basis of the Gopher system: 1) information search using logical queries; 2) search by keywords; 3) the idea of hierarchical directories; 4) binary search? 53. What is the WAIS system based on: 1) information retrieval using logical queries; 2) searching by keywords; 3) on the idea of hierarchical directories; 4) on binary search? 1. Which programming language is closely related to the UNIX OS: 1) HTML; 2) Pascal; 3) Si; 4) Java? 2. UNIX OS is: 1) a network OS for working on the Internet; 2) multifunctional network OS universal significance; 3) OS for closed systems; 4) OS to support Windows environment. 3. What command in UNIX OS can you find out the name of the current directory: 1) is; 2) change directory; 3)cat; 4) pwd (print working directory)? 4. The Is command in UNIX OS is used: 1) to change the working directory; 2) to combine several files for printing; 3) to display the contents of the directory; 4) to copy files. 5. Changing the working directory in UNIX OS is done with the command: 1) cd; 2)cat; 3) pwd; 4) is. 6. What the cat command does in UNIX OS: 1) determines the name of the current directory; 2) printing; 3) combines files and sends the result to output; 4) cuts out pieces of data from a file? 7. What are metacharacters used for in UNIX OS: 1) to destroy all files; 2) to destroy directories; 3) to substitute any strings and characters into file names; 4) to rename files? 8. How a program channel is formed in the UNIX OS: 1) by assigning the standard output of one command to the input of the next command; 2) redirecting the command output with append; 3) introducing an arbitrary string into the command; 4) combining teams? 9. To receive mail in the UNIX OS, enter the command: 1) write; 2) mail; 3) delete; 4) who.
 Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned
Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned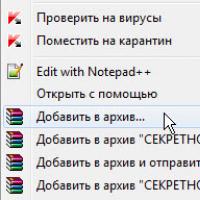 How to put a password on a folder on a Windows computer without and with programs
How to put a password on a folder on a Windows computer without and with programs Pluton – Free Bootstrap HTML5 One Page Template
Pluton – Free Bootstrap HTML5 One Page Template History of the ZX Spectrum: Myths and reality New Spectrum
History of the ZX Spectrum: Myths and reality New Spectrum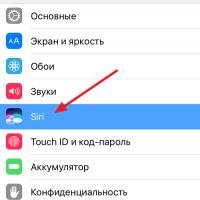 Voice assistant Siri from Apple Siri functions on iPhone 6s
Voice assistant Siri from Apple Siri functions on iPhone 6s How to roll back to a previous version of iOS?
How to roll back to a previous version of iOS?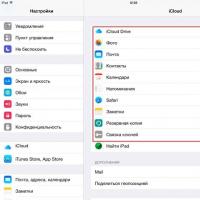 Unlock iPad in four days
Unlock iPad in four days