How to protect your mobile phone from hacking. Protecting your phone from loss or theft - Android Device Manager How to protect your smartphone from theft
In this article I will tell you how you can insure yourself against possible loss of your phone. After following the instructions you will be able to:
- find your Android phone or tablet(you can find out the approximate location of the device)
- remotely lock phone/tablet
- through the Internet remove personal data from the device
For the service to work you need:
- active
- Internet access on the phone
- geolocation is enabled on the device (GPS)
Internet access is needed to communicate with the phone, GPS to determine and transmit coordinates, Google account to manage the service " Android Remote Control »
If all this is there, then you can proceed to setting up the “Remote Android management" First, let's set up the phone, you need to enable remote control. To do this, go to the menu, “Settings” - “Google” settings - “Security”. Here we enable the items “Remote device search” and “Remote lock and reset”:





Let's also check whether the geolocation function (GPS) is enabled. To do this, go to “Menu” - “Settings” - “Location” - move the switch to the “ON position”




And also on the phone must be turned on Mobile Internet or WiFi. This completes the setup.
Now let's check the functionality of the service. Go to your computer or laptop and open the page in the browser https://www.google.com/android/devicemanager?hl=ru. Enter data here Google account from your Android and after that the service page will load:
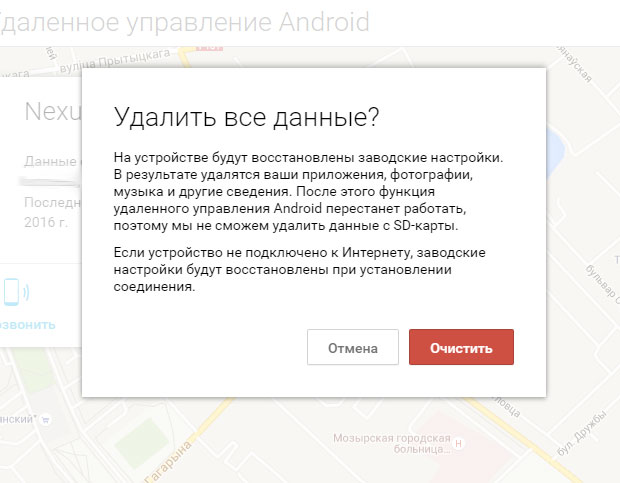
Here we see the location of our device and 3 available functions: ring, block, clear.
If your phone or tablet is not visible in the service, then it may be hidden in Google Play; to display it, you must enable the “Show in menu” function on the page play.google.com/settings
For the simplest test, click “Ring”; if everything is configured correctly, the phone should ring.

When you select the "Block" function, you can set New Password, for improved locking. You can also set a message that will be displayed on the lock screen, for example “Reward for return! My number is +77-777-777.” And you can also set an allowed phone number, this is the only number that can be called and it will be displayed on the lock screen.

And the last function is phone cleaning. If there is information on the phone that should not fall into the hands of other people and there are doubts that the phone will be found, then you can delete all data on the phone.
That’s all, if you have any questions, you can ask them in the comments :)
Why prepare your device for theft or loss?
Loss or theft is always a surprise. By preparing your device in advance, if it is lost, you can:
Protect your personal data (for example, photographs) from unauthorized people;
Monitor the location of the device;
Prevent anyone from using your device who found or stole it.
Step One: Lock Your Screen
For what
If the screen is locked, you cannot use your device or view its contents. To view photos, read SMS or do anything with the device, you need to know the password or PIN code.
Go to Settings → Lock screen & security → Screen lock type or Screen lock → Set a lock. We recommend using a password (numbers and letters) or PIN code (minimum five digits). If your device has a fingerprint sensor or an iris scanner, you can use them.
Now every time you turn on the screen you need to unlock it.
Step Two: Encrypt the Memory Card
For what
If you store important files on the card, encryption will protect them - they will only be read on the device where the card was encrypted.
If there are no important files on the memory card, or there is no card in the device, then it is not necessary to encrypt it.
Go to Settings → Biometrics & Security, Security or Lock Screen & Security → Encrypt SD Card (Encrypt External Memory Card) → Encrypt SD Card or Encrypt External Memory Card → Encryption will begin.
Now if you insert the card into another device (laptop, smartphone...), the files will not be read.

Step three: enable PIN code request on SIM card
For what
No one will be able to call or send SMS from your SIM card until they enter the correct PIN code. If the PIN code is entered incorrectly three times, the SIM card will be blocked.
In most cases, the PIN code request is disabled on the SIM card. To enable it, you need to know your current PIN code. The current PIN code is indicated on the plastic card into which the SIM card was inserted upon purchase.
If you do not know the current PIN code, replace the SIM card with your operator. The number will remain the old one, but the PIN code will be new.
Go to Settings → Biometrics & security, Security or Lock screen & security → SIM card lock or Other security settings → Set up SIM lock → Turn on lock and change PIN the code is more complex.
Now, when you turn on the device, you will need to enter the PIN code from the SIM card.

Mobile gadgets are made to simplify the life of any person, and their lack of control allows you to work or play with them in public places, increasing the risk of their loss, both theft and loss. But one way or another, developers think about their users and try to help as much as possible with the search or to remotely block the gadget. For this purpose, various software for iPhone and Android, which can, if a gadget is lost, either quickly find it by coordinates or completely block it. Such developments turn out to be very useful, because they prevent the next criminal implementation of such smartphones.
How to protect against theft and loss of iPhone
The following functions will help you find and return your iPhone or iPad:
- iCloud
- Activation Lock
- Find iPhone app
January 29, 2015 Apple company has filed a wonderful patent application for a new security technology for the iPhone, in order to reduce the possibility of theft of the smartphone as much as possible. This is called Apple going crazy. If the Cupertino company really implements these technologies, not a single robber would think of stealing someone’s smartphone. So what does this technology do? Every robber thinks straightforwardly: I’ll turn off the device so that they don’t start calling me or, even worse, they won’t track me, and he thinks correctly. This technology proposes to introduce special password before turning off, this is where the robber was caught. While he enters different combinations, the iPhone can be tracked ten times. Moreover, the code is not just a set of numbers, it is a code word. It is possible that this technology will use a fingerprint, which will make it even more difficult to hack a mobile device. Now that many developments are already in full use and there is even a face id system, you don’t have to worry too much about your device and data, but it’s better to play it safe and protect your gadget as much as possible, and we’ll now tell you in more detail how to do this.
If your smartphone is stolen, and there is no second one nearby, then you must immediately go to the icloud.com website from any device and put your gadget in lost mode. This mode locks the display with a four-character password and displays your phone number to help you return your device. During such a blocking, the use of the gadget is impossible until the device is unlocked by the owner.

Using this service, you can display various messages on the screen, for example: “ This phone is wanted by the finder, please call 99-99-99” and the finder will have a 90% chance of returning the device to you.
Activation Lock
This feature also helps protect your iPhone if it ends up in the wrong hands. When it is enabled, you will need to enter correct Apple ID and password. Even if all device data is erased and important information, the function will continue to work as if nothing had happened and cannot be disabled without your permission. This function turns on automatically when setting up the Find Iphone service.

Find iPhone app
How to protect against theft and loss of Android
- Remote control
- Security and location apps
Using the service from Google, you can protect personal data so that no one can use it, as well as find out the location of the gadget and perform some other actions that significantly worsen the situation of the one who stole the phone. It is also possible to send messages to the device, return it with a text for a reward, call the phone, erase data, etc. All this can be done by going to the service via the link google.com/android/devicemanager

By enabling remote control on your device, you can control it from anywhere, but to do this you must use google service or special programs and applications.

Applications to protect your Android smartphone
Nowadays, many different applications are being developed, by installing them on your phone, you can easily track it or control various functions. This is done specifically for security and so that anyone can quickly find or limit the use of a smartphone. All of them allow you to send messages, make calls, block certain functions, or covertly launch the camera to take a photo of the thief.

Protection applications that can be downloaded from the Play Market
- Lost Android
- Prey Anti-Theft
- Find My Phone
- Where's My Droid
Cases of ransomware attacks on users and entire organizations have become more frequent. The recent massive attack, which killed more than 200,000 computers around the world, was largely possible precisely because of poor security mobile devices. Ten simple tips will help reduce the likelihood of your smartphone or tablet being hacked.
1. Update your operating system
Install new OS versions immediately. If this does not happen automatically, pay attention to notifications and do not delay. Updates often contain fixes for recently discovered firmware vulnerabilities.
2. Install new versions of applications
Updates mobile applications also often do not happen automatically. At the same time, they contain amendments to improve the security of your device.
3. Don’t upload just anything
Experts recommend paying close attention to information about the application developer and the download source. This is especially true for free download links that you randomly receive on the Internet. Trust only trusted sources. Also, you should not click on suspicious links that promise, for example, .
4. Turn off Wi-Fi and Bluetooth
Remember to deactivate Wi-Fi and other connections when you are not using them. Access points open the way to remotely logging into your smartphone or tablet. It is much more difficult for attackers to gain access to a device whose wireless connection functions are disabled.
5. Pay attention to text messages
Immediately delete messages from unknown senders, especially those containing links or requests for any of your data. Do not go to suspicious sites (for example, those promising a reward for filling out a survey or watching a video), even if the link came from your friend. It's likely his phone was hacked.
6. Use strong passwords
Of course, it's easier to remember obvious passwords (like your date of birth or just 12345), but they can be just as obvious to hackers. All combinations based on personal information, words from any language, significant dates and so on are relatively easy to come up with. It is best to use randomly generated sets of numbers and letters of different case. Also, look at which ones will help you manage passwords effectively and securely.
7. Set up remote access
The two most popular mobile platforms have features « Remote control Android" and "Find iPhone". They will allow you to find out the location of the stolen device and erase personal data and files from it. Here are the instructions if you have lost your smartphone.
8. Enable encrypted backup
A daily encrypted copy of data from your phone will help you restore information if your device is lost or stolen. - this is the key to the safety of your data.
9. Log out of your accounts
It's easier to never log out of your account on frequently visited sites and apps, but it increases the risk of hacking. Instead of pressing “Save password” and “Stay logged in”, it is better to enter your password every time and be safe.
10. Be careful with public Wi-Fi
An open access point without a password is a favorite method of hackers. And even password-protected Wi-Fi can be dangerous. By connecting to your device, an attacker will be able to get literally everything that is on the gadget and see everything that you do on it.
To determine whether a device has been hacked, you should pay attention to signs such as fast discharge, applications that open and close on their own, too much mobile traffic consumption.
Google, Apple, Microsoft and many other technology companies have a long history of improving user security. They have created great tools with which they have improved our security.
The developments of these companies allow us to protect our devices as much as possible and they allow us to be confident that user data, both on the phone and in the cloud, will be protected.
You also need to understand that responsibility for the security of personal data largely falls on the user himself. If you want your personal data to be protected, you need to use all possible means of protection from unauthorized persons. Protected data must be difficult to obtain and also difficult to decrypt. Android smartphones have some cool features that will make you feel safe.
To begin with, the simplest thing you can do is put a password on your smartphone. Having a password allows you to restrict access to data on your phone or in the cloud. If you left your phone on the table, or if you lost your phone or it was stolen, a password will help you protect your data. True, in some cases even this does not help.
A six-digit PIN is much more difficult to crack than a four-digit PIN, but even it can be cracked under certain circumstances, such as if the attacker has special password-guessing equipment.
Long alphanumeric passwords open up the possibility that they will take a very long time to guess the password. But at the same time, entering a long, complex password on your phone is inconvenient. Therefore, in addition to the password, there are alternative methods of protection.
Encrypt all your local data and protect your data in the cloud with two-factor authentication on your accounts.
Android 7.0 Nougat and newer versions introduced an encryption system that differs from what was in Android smartphones earlier. Now each file is encrypted separately.
Also all accounts must have strong password and two-factor authentication, if it is possible to link an authenticator or SMS notification.
Don't use the same password on multiple sites. But in order not to forget your passwords, use a password manager (Smart Lock).
Don't follow unclear links
You should never open suspicious links or messages from unknown numbers. If you need to receive a letter from a specific person by email, then before doing so it is better to ask for his email address.
But at the same time, you can open links of verified users on Twitter or VK with peace of mind.
Why you should care about protecting your data
The reasons that I will indicate are not far-fetched or fictitious. For example, in 2015, the Stagefright exploit could cause an Android phone to freeze using SMS and allow attackers to gain access to your file system, where the script could install malware without any problems. It later turned out that a JPG or PDF file does the same thing on an iPhone.
The exploit was quickly fixed, but there is confidence that another similar exploit will be found, since errors in the code are still found to this day, for example, such as .
Install only verified applications
For most, Play Store is the only source where you can download applications. If an application or link directs you to install it from some strange location, do not click on the link until you know what that site is.
In addition, you can enable the item in the settings "do not install applications from unknown sources", but only if you are confident in the reliability of the application.
But if you install applications from Google Play, this does not mean that the applications are 100% safe, because we remember cases when malicious utilities ended up in the application store.
If you need to install applications from a third-party source, then you should make sure that you trust the source itself. In fact, malware that exploits system vulnerabilities can only appear if you have approved the installation. Roughly speaking, everything is in your hands.
***
With the release, Google released an update for Google play, which includes built-in Google Protect antivirus. In addition, installation from unknown sources has changed; now you can assign one or more applications from which the phone can download files. All these innovations indicate that Google is trying to protect both users and its operating system.

 Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned
Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned How to put a password on a folder on a Windows computer without and with programs
How to put a password on a folder on a Windows computer without and with programs Pluton – Free Bootstrap HTML5 One Page Template
Pluton – Free Bootstrap HTML5 One Page Template History of ZX Spectrum: Myths and reality New Spectrum
History of ZX Spectrum: Myths and reality New Spectrum Voice assistant Siri from Apple Siri functions on iPhone 6s
Voice assistant Siri from Apple Siri functions on iPhone 6s How to roll back to a previous version of iOS?
How to roll back to a previous version of iOS? Unlock iPad in four days
Unlock iPad in four days