An objective (alphabetical) approach to measuring information. Topic: Different approaches to measuring the amount of information. Take home: notes, tasks
1. Measure the information volume of the message “Hurray! Soon New Year!” in bits, bytes, kilobytes (KB), megabytes (MB).
Note: The text is considered to be typed using a computer; one character of the alphabet carries 1 byte of information. Space is also a character in the alphabet with a capacity of 256 characters.
2. Measure the approximate information capacity of one page of any of your textbooks, the entire textbook.
Note: To complete the task, take a textbook on your favorite subject, count the number of lines on the page, the number of characters per line, including spaces. Remember that one alphabet character carries 1 byte of information. By multiplying the resulting values, you will find the information capacity of one textbook page (in bytes).
3. How many of these textbooks can fit on a 1.44 MB floppy disk or on a 1 GB hard drive?
4. In the children's game “Guess the Number,” the first participant guesses an integer from 1 to 32. The second participant asks the questions: “Is the guessed number greater than ___?” With the right strategy, how many questions guarantee a guess?
Note: Ask the question in such a way that information uncertainty (the number of options) is reduced by half.
5. The poison is in one of the 16 glasses. How many units of information will a message about a glass of poison contain?
6. How many bits of information does the message that a “queen of spades” was taken from a deck of 32 cards?
7. There are two lotteries: “4 out of 32” and “5 out of 64.” The message about the results of which lottery contains more information?
8. An information message with a volume of 1.5 KB contains 3072 characters. How many characters does the alphabet with which this message was written contain? (Explanation of the solution to the problem on the board).
10. Information flow speed – 20 bits/sec. How long will it take to transfer 10 kilobytes of information?
11. Compare (put a relation sign)
o 200 bytes and 0.25 KB.
o 3 bytes and 24 bits.
o 1536 bits and 1.5 KB.
o 1000 bits and 1 KB.
o 8192 bytes and 1 KB.
12. There are 32 balls in the lottery drum. How much information does the message about the first number drawn contain (for example, number 15 was drawn)?
13. When playing dice, a die with six sides is used. How many bits of information does the player receive with each die roll?
14. A book typed using a computer contains 150 pages; each page has 40 lines, each line has 60 characters. How much information is in the book?
15. Calculate the amount of information contained in A. Dumas’ novel “The Three Musketeers” and determine how many similar works can be placed on one laser disc? (590 pages, 48 lines per page, 53 characters per line).
16. On a 100 MB disk, information is prepared for display on the display screen: 24 lines of 80 characters each, this information fills the entire screen. What part of the disk does it occupy?
17. There are 16 shelves of books in the school library. Each rack has 8 shelves. The librarian told Petya that the book he needed was on the fifth rack on the third shelf from the top. How much information did the librarian give to Petya?
18. There are 7 colored pencils in the box. How much information does the message that a red pencil was taken from the box contain?
19. How much information does the message convey: “The meeting is scheduled for September.”
20. The message takes 3 pages of 25 lines. Each line contains 60 characters. How many characters are in the alphabet used if the entire message contains 1125 bytes?
21. Eustace needs to convey the following message:
Dear Alex! I sincerely congratulate you on
Laboratory work №2.
Goal of the work:
Methodical instructions.
Information measurement tasks
1. Measure the information volume of the message “Hurray! New Years is soon!" in bits, bytes, kilobytes (KB), megabytes (MB).
Note: The text is considered to be typed using a computer; one character of the alphabet carries 1 byte of information. Space is also a character in the alphabet with a capacity of 256 characters.
2. Measure the approximate information capacity of one page of any of your textbooks, the entire textbook.
Note: To complete the task, take a textbook on your favorite subject, count the number of lines on the page, the number of characters per line, including spaces. Remember that one alphabet character carries 1 byte of information. By multiplying the resulting values, you will find the information capacity of one textbook page (in bytes).
3. How many of these textbooks can fit on a 1.44 MB floppy disk or on a 1 GB hard drive?
4. In the children's game “Guess the Number,” the first participant guesses an integer from 1 to 32. The second participant asks the questions: “Is the guessed number greater than ___?” With the right strategy, how many questions guarantee a guess?
Note: Ask the question in such a way that information uncertainty (the number of options) is reduced by half.
5. The poison is in one of the 16 glasses. How many units of information will a message about a glass of poison contain?
6. How many bits of information does the message that a “queen of spades” was taken from a deck of 32 cards?
7. There are two lotteries: “4 out of 32” and “5 out of 64.” The message about the results of which lottery contains more information?
8. An information message with a volume of 1.5 KB contains 3072 characters. How many characters does the alphabet with which this message was written contain? (Explanation of the solution to the problem on the board).
10. Information flow speed – 20 bits/sec. How long will it take to transfer 10 kilobytes of information?
11. Compare (put a relation sign)
o 200 bytes and 0.25 KB.
o 3 bytes and 24 bits.
o 1536 bits and 1.5 KB.
o 1000 bits and 1 KB.
o 8192 bytes and 1 KB.
12. There are 32 balls in the lottery drum. How much information does the message about the first number drawn contain (for example, number 15 was drawn)?
13. When playing dice, a die with six sides is used. How many bits of information does the player receive with each die roll?
14. A book typed using a computer contains 150 pages; each page has 40 lines, each line has 60 characters. How much information is in the book?
15. Calculate the amount of information contained in A. Dumas’ novel “The Three Musketeers” and determine how many similar works can be placed on one laser disc? (590 pages, 48 lines per page, 53 characters per line).
16. On a 100 MB disk, information is prepared for display on the display screen: 24 lines of 80 characters each, this information fills the entire screen. What part of the disk does it occupy?
17. There are 16 shelves of books in the school library. Each rack has 8 shelves. The librarian told Petya that the book he needed was on the fifth rack on the third shelf from the top. How much information did the librarian give to Petya?
18. There are 7 colored pencils in the box. How much information does the message that a red pencil was taken from the box contain?
19. How much information does the message convey: “The meeting is scheduled for September.”
20. The message takes 3 pages of 25 lines. Each line contains 60 characters. How many characters are in the alphabet used if the entire message contains 1125 bytes?
21. Eustace needs to convey the following message:
Dear Alex! I sincerely congratulate you on
Successful passing of the computer science exam.
Laboratory work No. 2.
Measuring the amount of information
Goal of the work: teach how to solve problems quantitative measurement information volume of text information.
Methodical instructions.
Due to different approaches to defining information, there are two approaches to measuring information.
Subjective (substantive) approach
In this approach, information is information and knowledge that a person receives from various sources. Thus, a message is informative (contains non-zero information) if it adds to a person's knowledge.
With a subjective approach, the information content of a message is determined by the presence in it new knowledge And understandability for a given person ( definition 1). Different people who receive the same message evaluate the amount of information contained in it differently. This happens because people’s knowledge about these events and phenomena before receiving the message was different. A message is informative for a person if it contains new information, and uninformative if the information is old and known. Thus, the amount of information in a message depends on how new the message is for the recipient and is determined by the amount of knowledge that the message carries to the person receiving it.
From the point of view of information as novelty, we cannot estimate the amount of information contained in a new discovery, a musical style, a new theory of development.
The subjective approach is based on the fact that obtaining information, increasing it, means decreasing ignorance or information uncertainty (definition 2).
The unit of measurement for the amount of information is called bit( bit – binarydigit), which means binary digit.
The amount of information is the number of bits in the message.
A message that reduces information uncertainty (knowledge uncertainty) by half carries for him 1 bit information.
What is “information uncertainty”?
Information uncertainty about some event is the number of possible outcomes of the event.
Example_1: The book lies on one of two shelves - top or bottom. The message that the book is on the top shelf reduces the uncertainty exactly by half and carries 1 bit of information.
The message that one of two equally probable events has occurred carries 1 bit information.
Example_2: Nesterov lives on Leningradskaya Street. We received a message that his house number was an even number, which reduced the uncertainty. After receiving such information, we began to know more, but information uncertainty remained, although it was halved.
Example_3: Your friend lives in a 16-story building. How much information does the message that a friend lives on the 7th floor contain?
Solution : Information uncertainty (the number of possible outcomes of an event) is 16. We will ask questions that can only be answered “yes” or “no.” We will pose the question so that each answer brings 1 bit of information, i.e. reduced information uncertainty by half.
We ask questions: - Does your friend live above the 8th floor?
After this answer, the number of options decreased by half, therefore, information uncertainty decreased by half. 1 bit of information received.
Does your friend live above the 4th floor?
The number of options has decreased by half, and 1 more bit of information has been received.
Does your friend live above the 6th floor?
After this answer, there are two options left: the friend lives either on the 7th floor or on the 8th floor. 1 more bit of information received.
Does your friend live on the 8th floor?
All clear. A friend lives on the 7th floor.
Each answer reduced information uncertainty by half. A total of 4 questions were asked. 4 bits of information received. The message that a friend lives on the 7th floor of a 16-story building carries 4 bits of information.
A scientific approach to evaluating messages was proposed back in 1928 by R. Hartley.
Let some message contain information that one of N equally probable events occurred ( equiprobability means that no event takes precedence over others). Then the amount of information contained in this message is x bits and the number N are related by the formula:
where x is the amount of information or informativeness of the event (in bits);
N – number of equally probable events (number of possible choices).
This formula is an exponential equation for the unknown x. Solving the equation, we obtain a formula for determining the amount of information contained in a message that one of N equally probable events has occurred, which has the form:
x = log 2N
logarithm of N to base 2.
If N is equal to an integer power of two, then such an equation can be solved easily, otherwise a table of logarithms will help you solve the problem.
If N = 2 (choice between two possibilities), then x = 1 bit.
returning to example_3, if we use the formula to calculate the amount of information in a message that a friend lives on the 7th floor of a 16-story building, then x = log 2 16 = 4 bits.
Example_4: How much information is conveyed by the message that the meeting is scheduled for July?
Solution : There are 12 months in a year, therefore, the number of equally probable events or the number of possible choices is N = 12. Then the amount of information x = log 2 12. To solve this equation, use a table of logarithms or a calculator.
Answer: x = 3.58496 bits.
Example_5: When guessing an integer in the range from 1 to N, 8 bits of information were obtained. What is N equal to?
Solution: In order to find a number, it is enough to solve the equation N = 2 x, where x = 8. Since 2 8 = 256, then N = 256. Therefore, when guessing any integer in the range from 1 to 256, we get 8 bits of information.
Situations in which the value of N is precisely known are rare. Try using this principle to calculate the amount of information obtained when reading a page of a book. This is impossible to do.
1. Measure the information volume of the message “Hurray! New Years is soon!" in bits, bytes, kilobytes (KB), megabytes (MB).
Note: The text is considered to be typed using a computer; one character of the alphabet carries 1 byte of information. Space is also a character in the alphabet with a capacity of 256 characters.
2. Measure the approximate information capacity of one page of any of your textbooks, the entire textbook.
Note: To complete the task, take a textbook on your favorite subject, count the number of lines on the page, the number of characters per line, including spaces. Remember that one alphabet character carries 1 byte of information. By multiplying the resulting values, you will find the information capacity of one textbook page (in bytes).
3. How many of these textbooks can fit on a 1.44 MB floppy disk or on a 1 GB hard drive?
4. In the children's game “Guess the Number,” the first participant guesses an integer from 1 to 32. The second participant asks the questions: “Is the guessed number greater than ___?” With the right strategy, how many questions guarantee a guess?
Note: Ask the question in such a way that information uncertainty (the number of options) is reduced by half.
5. The poison is in one of the 16 glasses. How many units of information will a message about a glass of poison contain?
6. How many bits of information does the message that a “queen of spades” was taken from a deck of 32 cards?
7. There are two lotteries: “4 out of 32” and “5 out of 64.” The message about the results of which lottery contains more information?
8. An information message with a volume of 1.5 KB contains 3072 characters. How many characters does the alphabet with which this message was written contain? (Explanation of the solution to the problem on the board).
10. Information flow speed – 20 bits/sec. How long will it take to transfer 10 kilobytes of information?
11. Compare (put a relation sign)
o 200 bytes and 0.25 KB.
o 3 bytes and 24 bits.
o 1536 bits and 1.5 KB.
o 1000 bits and 1 KB.
o 8192 bytes and 1 KB.
12. There are 32 balls in the lottery drum. How much information does the message about the first number drawn contain (for example, number 15 was drawn)?
13. When playing dice, a die with six sides is used. How many bits of information does the player receive with each die roll?
14. A book typed using a computer contains 150 pages; each page has 40 lines, each line has 60 characters. How much information is in the book?
15. Calculate the amount of information contained in A. Dumas’ novel “The Three Musketeers” and determine how many similar works can be placed on one laser disc? (590 pages, 48 lines per page, 53 characters per line).
16. On a 100 MB disk, information is prepared for display on the display screen: 24 lines of 80 characters each, this information fills the entire screen. What part of the disk does it occupy?
17. There are 16 shelves of books in the school library. Each rack has 8 shelves. The librarian told Petya that the book he needed was on the fifth rack on the third shelf from the top. How much information did the librarian give to Petya?
18. There are 7 colored pencils in the box. How much information does the message that a red pencil was taken from the box contain?
19. How much information does the message convey: “The meeting is scheduled for September.”
20. The message takes 3 pages of 25 lines. Each line contains 60 characters. How many characters are in the alphabet used if the entire message contains 1125 bytes?
21. Eustace needs to convey the following message:
Dear Alex! I sincerely congratulate you on
Successful passing of the computer science exam.
I wish you continued success. Yours, Eustace.
The direction finder determines the location of the transmission if it lasts at least 3 minutes. At what speed (bit/s) should Eustace transmit the radio message?
22. Measure the information volume of the message “Hurray! The holidays are over!!” (from the point of view of a technical approach, that is, without taking into account the meaning of the message). Express this volume in bits, bytes, kilobytes.
23. Measure the approximate information capacity of 1 page of the textbook, the entire textbook. How many of these textbooks can fit on a floppy disk with a capacity of 360 KB, 1.44 MB, or on a hard drive of 420 MB, 6.4 GB?
Information as removed uncertainty
24. Determine how many bits of information are carried by the message that the traffic light is green.
25. Suppose the probability that you will receive a grade of “5” for the test is 0.6; the probability of getting “4” is 0.2; the probability of getting “3” is 0.2. Determine how many bits of information the message about the results of the test will carry in each of the possible cases.
26. Given:
Number of colors = 2
Picture size = 7*14 pixels
27. Given:
Number of colors = 8
Picture size = 17*24 pixels
28. Assuming that one character is encoded by one byte, calculate in bytes the amount of information contained in the phrase: “Patience and work will grind everything down.
29. (Task A2 demo version 2004)
30. Assuming that each character is encoded by one byte, estimate information volume sentences: “My uncle had the most honest rules, When he was seriously ill, He forced himself to be respected And he couldn’t think of anything better.”
32. A message is received, the information volume of which is 32 bits. What is this volume in bytes?
Solution.
Let's use the formulas:
In our case:
Substituting values (8) and (9) into (5), we obtain that: 2 15 = 2 14 *i, from which i=2.
Then according to formula (6):<Количество цветов>=N = 2 i =2 2 =4, which corresponds to answer No. 4.
Answer: 4.
35. Assuming that each character is encoded by one byte, estimate the information volume of the following sentence in KOI-8 encoding (in bytes):
Meteorologists predicted rain today.
36. Assuming that each character is encoded with 16 bits, estimate the information volume of the following sentence in Unicode encoding (in bytes):
Each character is encoded with eight bits.
37. How many different sequences of characters “a” and “b” are there exactly 10 characters long?
38. There are two rectangular areas of spectator seats in the auditorium: one is 10x12, and the other is 17x8. What is the minimum number of bits required to encode each location in automated system?
39. The message is transmitted in seven-bit code. What is its information volume in bytes if it is known that 2000 characters were transmitted?
40. In the alphabet of a formal (artificial) language there are only two letter signs (“0” and “X”). Each word of this language always consists of five letters. What is the maximum number of words possible in this language?
42. There is a test, the size of which is 20 kilobytes (each test page has 40 lines of 64 characters per line, 1 character takes 8 bits). Determine the number of pages in the test.
43. How many bytes are in 32 GB?
Creative task.
Let there be a 1.44 MB storage medium. You need to record a photo on it with dimensions of 1024 * 768 pixels and a color depth of 24 bits. Will it be possible to do this? If not, what color depth can I use? How many colors will it include? Prepare the solution to the problem in the ET Excel environment.
Laboratory work No. 3. Encryption of text information.
Goal of the work: study of the simplest methods of cryptographic information protection.
Brief information from the theory.
Simple substitution ciphers
Caesar Cipher System- a special case of a simple substitution cipher. The method is based on replacing each letter of the message with another letter of the same alphabet, by shifting from the original letter by K letters.
Famous phrase of Julius Caesar
VENI VI D I VICI, where
| A | B | C | D | E | F | G | H | I | G | K | L | M |
| N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
I came, I saw, I conquered, encrypted with this method, is converted to
when shifted 4 characters to the left.
Greek writer Polybius 100 years BC. the so-called polybian square size 5*5, filled with the alphabet in random order. The Greek alphabet has 24 letters, and the 25th character is the space. For encryption, a letter of the text was found on the square and the letter located below it in the same column was written into the encrypted message. If a letter was in the bottom row of the table, then the top letter from the same column was taken.
| M | T | L | E | X |
| A | K | F | Q | Y |
| N | B | R | O | W |
| C | J | H | D | P |
| U | I | S | G | V |
Viginère encryption scheme. The Viginère table is a square matrix with n 2 elements, where n is the number of characters of the alphabet used. The figure shows the top part of the Viginère table for the Cyrillic alphabet. Each line is obtained by cyclically shifting the alphabet by a character. For encryption, a letter key is selected, according to which a working encryption matrix is formed.
| A | b | V | G | d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I |
| b | V | G | d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A |
| V | G | d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b |
| G | d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b | V |
| d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b | V | G |
| e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b | V | G | d |
| Etc. up to the 33rd line.. |
Viginaire table
This is done as follows. The first row and those rows whose first letters correspond to the letters of the key are selected from the complete table. The first line is placed first, and below it are the lines corresponding to the letters of the key in the order that these letters appear in the encryption key. An example of such a working matrix for the “book” key is given at Rice. 3.1.3.
The encryption process is carried out as follows:
1. Under each letter of the encrypted text, the letters of the key are written. The key is repeated the required number of times.
2. Each letter of the encrypted text is replaced along the submatrix with letters located at the intersection of the lines connecting the letters of the encrypted text in the first row of the submatrix and the key letters located under them.
3. The received text can be divided into groups of several characters.
For example, let's say you want to encrypt a message: The maximum allowable price is five hundred rubles. a piece. In accordance with the first rule, we write down the letters of the key under the letters of the encrypted text. We get:
The maximum allowable price is five hundred rubles. a piece
bookbooknigaknigak nigak nigaknigaknigak nigak nigak
| A | b | V | G | d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I |
| To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b | V | G | d | e | e | and | h | And | th |
| n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b | V | G | d | e | e | and | h | And | th | To | l | m |
| And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b | V | G | d | e | e | and | h |
| G | d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I | A | b | V |
| A | b | V | G | d | e | e | and | h | And | th | To | l | m | n | O | P | R | With | T | at | f | X | ts | h | w | sch | ъ | s | b | uh | Yu | I |
Next, direct encryption is carried out in accordance with the second rule, namely: we take the first letter of the encrypted text (M) and the corresponding key letter (K); by the letter of the encrypted text (M), we enter the working encryption matrix and select the letter under it located in the line corresponding to the letter of the key (K) - in our example, such a letter is H; The letter chosen in this way is placed in the ciphertext. This procedure is repeated cyclically until the entire text is encrypted.
Experiments have shown that when using this method, the statistical characteristics of the original text practically do not appear in the encrypted message. It is easy to see that replacement according to the Viginère table is equivalent to a simple replacement with a cyclic change of the alphabet, i.e. here we have a polyalphabetic substitution, and the number of alphabets used is determined by the number of letters in the key word. Therefore, the durability of such a replacement is determined by the product of the durability of a direct replacement by the number of alphabets used, i.e. number of letters in the key.
The text is decrypted in the following sequence:
1. The letters of the key are sequentially written above the letters of the ciphertext, and the key is repeated the required number of times.
2. in the row of the Viginère submatrix corresponding to the letter of the key, the letter corresponding to the sign of the ciphertext is found. The letter of the first row of the submatrix located under it will be the letter of the source text.
3. The received text is grouped into words according to their meaning.
It is easy to see that the procedures for both direct and inverse transformations are strictly formal, which allows them to be implemented algorithmically. Moreover, both procedures are easily implemented using the same algorithm.
One of the disadvantages of encryption using the Viginère table is that with a small key length, the encryption reliability remains low, and the generation of long keys is fraught with difficulties.
It is not advisable to choose keys with repeated letters, since this does not increase the strength of the cipher. At the same time, the key should be easy to remember so that it does not need to be written down. It is difficult to remember the sequence of letters that do not make sense.
In order to increase the strength of encryption, you can use improved versions of the Viginère table. Here are just a few of them:
· in all (except the first) rows of the table the letters are arranged in random order.
· Randomness of consecutive numbers is used as a key. Ten arbitrary rows are selected from the Viginère table, which are encoded with natural numbers from 0 to 10. These rows are used in accordance with the alternation of numbers in the selected key.
Many other modifications of the method are also known.
Permutation algorithm
This method consists in the fact that the characters of the encrypted text are rearranged according to certain rules within the encrypted block of characters. Let's consider some varieties of this method that can be used in automated systems.
The simplest permutation is to write the original text backwards and at the same time break the ciphergram into five letters. For example, from the phrase
LET IT BE THE WAY WE WANTED.
you get the following ciphertext:
ILETO KHIMKA KKATT EDUB TSUP
The last group (five) is missing one letter. This means that before encrypting the original expression, it should be supplemented with an insignificant letter
(for example, O) to a multiple of five:
LET-BE-TAKKA-KMYKHO-TELIO.
Then the ciphergram, despite such minor changes, will look different:
OILET OKHYMK AKKAT TEDUB LTSUP
It seems nothing complicated, but when decrypting it there are serious inconveniences.
During the American Civil War, the following code was in use: the original phrase was written in several lines. For example, fifteen letters each (filling the last line with insignificant letters).
P U S T B U D E T T A K K A
K M Y H O T E L I K L M N O P
After this, the vertical columns were written in order into a line divided into five letters:
PKUMS YTHIO BTUED LEITK TLAMK NCOAP
If you shorten the lines and increase the number of lines, you get a lattice rectangle in which you can write the source text. But here a preliminary agreement between the addressee and the sender of the messages will be required, since the grid itself can be of different lengths and heights, you can write to it in rows, in columns, in a spiral there or in a spiral back, you can write along diagonals, and for encryption you can take different directions too.
Complex substitution ciphers
Gronsfeld cipher consists of modifying the Caesar cipher with a numeric key. To do this, write down the digits of the numeric key under the letters of the message. If the key is shorter than the message, then its recording is repeated cyclically. The encrypted message is received in approximately the same way as in the Caesar cipher, but not one hard-coded offset is used, but fragments of the key.
Let a group of three numbers – 314 – be used as a key, then the message
TOP SECRET
3 1 4 3 1 4 3 1 4 3 1 4 3 1 4 3 1 4
F P E S B Z O S S A H Z L F Z U S S
IN polyalphabetic substitution ciphers To encrypt each character of the original message, its own simple substitution cipher (its own alphabet) is used.
| A | ABVGDEYZHZIKLMNOPRSTUFHCHSHSHSHYYYYUYA_ |
| B | _ABVGDEYZHZIKLMNOPRSTUFHCHSHSHSHYYYYAY |
| IN | I_ABVGDEYZHZIKLMNOPRSTUFHCHSHSHSHYYYEYU |
| G | YUYA_ABVGDEYZHZIKLMNOPRSTUFHCHSHSHSHCHYYE |
| . | ………… |
| I | VGDEЁZHZIKLMNOPRSTUFHCHSHSHSHCHYYYYYYUYA_AB |
| _ | BVGDEYEZHZIKLMNOPRSTUFHCHSHSHSHYYEYUYA_A |
Each row in this table corresponds to one substitution cipher, similar to the Caesar cipher for the space-padded alphabet. When a message is encrypted, it is written out in a line, with the key underneath it. If the key is shorter than the message, it is repeated cyclically. The encrypted message is obtained by finding a character in a table column by the letter of the text and the line corresponding to the letter of the key. For example, using the AGAVA key, from the message I’M COMING ON THE SIXTH we get the following encryption:
I'M ARRIVING ON THE SIXTH
AGAWAAGAVAAGAWAA
POIGZJYUWHEPTNGO
This operation corresponds to adding the ASCII codes of the message characters and the key modulo 256.
Exercise
Come up with 3 phrases, each with at least 7 words. Encrypt this phrase with all the listed types of encryption.
with hard drives that have a single partition, and this is when working with earlier versions Windows wastes a lot of disk space.
A section is, in essence, some part hard drive. If a disk contains only one partition, it is designated as C:. However, you can break HDD and into several sections, of any size, and assign each of them its own identifier letter.
This disk repartition will help better organize the placement of data and make it easier to create backup copies. For example, if you use for Reserve copy Zip drive with 100 MB cartridge, then optimal solution for you - preliminary saving of files in a hard disk partition of the same size. At least this will save you from the tedious sorting of data. The great thing about partitioning your disk is that you will have more free disk space.
Cluster disturbance
This additional space is obtained due to the location of data on the disk, which is stored in portions in certain structures of a fixed size - the so-called clusters. In DOS, Windows 3.x, and many other previous versions Windows 95 their sizes depend on the size of the partitions in which they are located, and usually range from 2 to 32 KB.
Since any file on the disk occupies at least one cluster, and the remaining space inside the latter is unfilled, therefore, the smaller the cluster size, the more efficiently the disk space is used. If your hard drive is full of myriads of small files, the losses add up. Let's say you received e-mail 500 messages, each of which is stored in its own small file on a 1.2 MB hard drive with one partition and the FAT16 file system. As a result, you lose approximately 8 MB of disk space. For comparison, if the files were stored in a 100 MB partition where the cluster size is 2 KB, then the disk space loss would be about 500 KB. To check the cluster size on a disk, run the ScanDisk utility: click the Start button and select the menu items Programs? Accessories? Utilities? ScanDisk (Programs? Accessories? System Tools? ScanDisk) , then select the drive and click on the “Launch” button. In the third line from the bottom in the “Results” field, the number of bytes in the cluster (also called the memory allocation unit) will appear. If you are using DOS, Windows 3.x, the original Windows 95, or Windows 95 upgraded with Microsoft Service Pack I (version 4.00.950A), you will need to partition your hard drive into smaller partitions to achieve smaller clusters .
When working with Windows 95 OSR2 (version 4.00.950B), another choice is possible. (To find out which version is installed, right-click on the My Computer icon, point to Properties, and select the General tab.) This version supports file system FAT32, which is a further development of FAT16, used by DOS and older versions of Windows 95 to track the location of files on the hard drive. FAT32 includes a number of new improvements, including increased maximum size partitions up to 2 TB (compared to the FAT16 limit of 2 GB) and very small clusters in large partitions - 4 KB for partitions up to 8 GB.
Thus, you can reduce the size of a cluster on a disk in two ways: using FAT32 or reducing partitions.
Disk partitioning is the hard way
DOS and Windows 95 systems come with two key utilities: Fdisk - deletes and creates partitions, Format - sets the file system. Both of them run in DOS mode and are located on the Windows 95 boot diskette.
Applying the Fdisk and Format utilities to a hard drive where information is already stored is not at all as pleasant as a walk in the park. So, before starting to create new partitions, Fdisk requires the removal of existing ones, and this entails the loss of all data. Therefore we have to do backups everyone necessary files and programs, so that you can later restore them to the disk with a new partition.
Before deleting partitions, use the Fdisk utility to select a repartition strategy. Insert the boot floppy disk into drive A: and restart your PC. IN command line type fdisk and click. In the Fdisk program menu that appears, select item 4 and see how this moment the hard drive is partitioned and what letter is assigned to each partition. There are three types of partitions. They are created in the following order.
Main section. It must contain an OS with a boot program. If you want your computer to be able to boot with more than one OS, you should create primary partitions for each of them. OS DOS and Windows 95 can have up to four main partitions on one disk, but only one of them can be active or bootable.
Additional section. After creating the main partition, you can create additional ones. To do this, you need to set the unused space as an additional partition, and then divide it into logical drives.
Logical drives. Each logical drive is assigned its own letter and, as a rule, applications and/or data are stored on them.”
Thus, after viewing the existing partitions, you can begin to repartition the hard drive. To destroy all existing partitions (first delete the logical drives in the additional partition, then this partition itself and only then the main one) from the Fdisk menu, select item 3. After that, restart the computer, select action 1 in the Fdisk menu and create new partitions. In this case, new letters will be assigned to the disks. If in the future any application does not work after repartitioning, then check its INI file and see if the drive letter in the file address needs to be changed. When you add a partition, your CD drive letter will also change.
After the partitions are in place, use the Format utility to set file systems for each of them. Depending on the selected Windows versions 95 will install FAT16 or FAT32. At Windows work 95 OSR2 you can specify the file system yourself.
The easy (but not cheap) way
If there is a lot of programs and data on the disk, but there is no convenient way If you save them while working with the Fdisk and Format utilities, you can make your life easier by spending some money.
Two great utilities can help you repartition your hard drive without moving or losing any data: Partition Magic from PowerQuest and Extra-Strength Partition-It from Quarterdeck.
These programs will save you hours of hard work and frustration. They will help you convert partitions from FAT16 to FAT32.
Windows 98 includes a utility for converting FAT16 to FAT32 - “Convert Disk to FAT32”. Although Microsoft claims that it is easy to use and safe, please read the appropriate Windows Help carefully before using it.
FAT32 saves precious space
| Cluster size | Estimated disk space loss when storing 500 small files |
Partition size when used | |
| FAT32 | FAT16 | ||
| 512 bytes | Very little | Less than 260 MB | Not provided |
| 2 KB | 500 KB | Not provided | 16-127 MB |
| 4 KB | 1 MB | 260 MB-8 GB | 128-255 MB |
| 8 KB | 2 MB | 8-16 GB | 256-511 MB |
| 16 KB | 4 MB | 16-32 GB | 512-1023 MB |
| 32 KB | 8 MB | 32-2048 GB | 1024-2048 MB |
Disks with a FAT16 file structure waste their space when you don't split them into small partitions. Usage file structure FAT32 significantly saves space on large disks
1. Measure the information volume of the message “Hurray! New Years is soon!" in bits, bytes, kilobytes (KB), megabytes (MB).
Note: The text is considered to be typed using a computer; one character of the alphabet carries 1 byte of information. Space is also a character in the alphabet with a capacity of 256 characters.
2. Measure the approximate information capacity of one page of any of your textbooks, the entire textbook.
Note: To complete the task, take a textbook on your favorite subject, count the number of lines on the page, the number of characters per line, including spaces. Remember that one alphabet character carries 1 byte of information. By multiplying the resulting values, you will find the information capacity of one textbook page (in bytes).
3. How many of these textbooks can fit on a 1.44 MB floppy disk or on a 1 GB hard drive?
4. In the children's game “Guess the Number,” the first participant guesses an integer from 1 to 32. The second participant asks the questions: “Is the guessed number greater than ___?” With the right strategy, how many questions guarantee a guess?
Note: Ask the question in such a way that information uncertainty (the number of options) is reduced by half.
5. The poison is in one of the 16 glasses. How many units of information will a message about a glass of poison contain?
6. How many bits of information does the message that a “queen of spades” was taken from a deck of 32 cards?
7. There are two lotteries: “4 out of 32” and “5 out of 64.” The message about the results of which lottery contains more information?
8. An information message with a volume of 1.5 KB contains 3072 characters. How many characters does the alphabet with which this message was written contain? (Explanation of the solution to the problem on the board).
10. Information flow speed – 20 bits/sec. How long will it take to transfer 10 kilobytes of information?
11. Compare (put a relation sign)
o 200 bytes and 0.25 KB.
o 3 bytes and 24 bits.
o 1536 bits and 1.5 KB.
o 1000 bits and 1 KB.
o 8192 bytes and 1 KB.
12. There are 32 balls in the lottery drum. How much information does the message about the first number drawn contain (for example, number 15 was drawn)?
13. When playing dice, a die with six sides is used. How many bits of information does the player receive with each die roll?
14. A book typed using a computer contains 150 pages; each page has 40 lines, each line has 60 characters. How much information is in the book?
15. Calculate the amount of information contained in A. Dumas’ novel “The Three Musketeers” and determine how many similar works can be placed on one laser disc? (590 pages, 48 lines per page, 53 characters per line).
16. On a 100 MB disk, information is prepared for display on the display screen: 24 lines of 80 characters each, this information fills the entire screen. What part of the disk does it occupy?
17. There are 16 shelves of books in the school library. Each rack has 8 shelves. The librarian told Petya that the book he needed was on the fifth rack on the third shelf from the top. How much information did the librarian give to Petya?
18. There are 7 colored pencils in the box. How much information does the message that a red pencil was taken from the box contain?
19. How much information does the message convey: “The meeting is scheduled for September.”
20. The message takes 3 pages of 25 lines. Each line contains 60 characters. How many characters are in the alphabet used if the entire message contains 1125 bytes?
21. Eustace needs to convey the following message:
Dear Alex! I sincerely congratulate you on
 Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned
Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned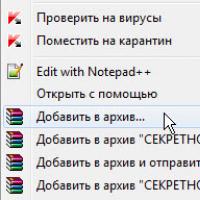 How to put a password on a folder on a Windows computer without and with programs
How to put a password on a folder on a Windows computer without and with programs Pluton – Free Bootstrap HTML5 One Page Template
Pluton – Free Bootstrap HTML5 One Page Template History of ZX Spectrum: Myths and reality New Spectrum
History of ZX Spectrum: Myths and reality New Spectrum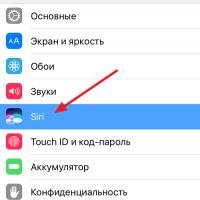 Voice assistant Siri from Apple Siri functions on iPhone 6s
Voice assistant Siri from Apple Siri functions on iPhone 6s How to roll back to a previous version of iOS?
How to roll back to a previous version of iOS?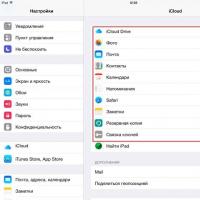 Unlock iPad in four days
Unlock iPad in four days