Download presentation system software. System software. Application packages
“Archive” - 8. Rights to sections For groups and individual users Inheritance. Document storage. Instructions, tasks and business processes. Automation of internal document flow. 12. Types of documents. 10. Organization of the educational process. Key Features. Alexander Bezborodov, head of the document management software development department.
"Programs" - Computer viruses And antivirus programs. Networking support. operating room Linux system created by a Finnish student. Menu bar: Student viruses. Programs can run in the background. What is the program? Programming systems. Example: C:\Program Files\Borland\Delphi7\project.exe.
"Software Development" - Cancel order. Implementation. J4. Internal structure of description of maturity levels. [Product selected]. The second stage is a structured approach to programming. Sales department. Department. J2. Safety system?
“Program Features” - High speed! Graphic editor. CD and dwd recording. It is possible to manually delete records about installed programs from system registry. But they don’t make stupid mistakes. It is possible to transfer files between servers bypassing the local host. The compression ratio for the ZIP format is 2-10% higher than that of PKZip/WinZip.
“Software” - Portability (mobility) is proposed to reflect: adaptability; ease of installation - installation; substitutability.
“Computer programs” - Application software. Author Sadykova I.Kh. Levels software configuration. Programming languages. Processing data on a computer. Why do you need an operating system? The user was able to edit and format text documents. The information processing process consisted of operations on numerical data.
system software (programs common use),
performing various auxiliary
functions, such as creating copies of the used
information, issuance reference information O
computer, checking the functionality of devices
computer, etc.
application software that provides execution
necessary work on PC: editing
text documents, creating drawings or
pictures, processing of information arrays and
etc.
tool software (programming systems),
ensuring the development of new programs for
computer in a programming language.
System software
These are general use programs and are not associated with a specificusing a PC and perform traditional functions:
planning and task management, input management
output, etc.
System software includes:
operating systems (this program is loaded into RAM
when you turn on the computer)
shell programs (provide more convenient and
a visual way to communicate with a computer than using
DOS command line, such as Norton Commander)
operating shells are interface systems that
used to create graphical interfaces,
multiprogramming, etc. Drivers (programs designed for
port management peripheral devices,
usually loaded into RAM when
starting the computer)
utilities (auxiliary or service
programs that present the user
a number of additional services)
Utilities include:
file managers or file managers
dynamic data compression tools
(allow you to increase the amount of information by
disk due to its dynamic compression) viewing and playback tools
diagnostic tools; controls allow
check your computer configuration and check
the performance of computer devices before
total hard drives
means of communication (communication
programs) are designed to organize exchange
information between computers
computer security tools
(backup, antivirus software).
Application software
Application packages are a systemprograms whose scope of application
are divided into problem-oriented,
general purpose and integrated packages
packages. Modern integrated
packages contain up to five functional
components: test and tabular
processor, DBMS, graphic editor,
telecommunications facilities.
Application software
Application software, for example, includes:MS OFFICE suite of office applications
Accounting systems
Financial analytical systems
Integrated office management packages
CAD systems (automated
design)
HTML or Web editors
Browsers – means of viewing Web pages
Graphic editor
Tool software
Tools or systemsprogramming are systems for
automation of new program development
in a programming language.
Borland Delphi - designed to solve
almost any application task
programming
Microsoft Visual C++ - this tool allows you to
develop any applications running in
OS type environment Microsoft Windows
File systems
All modern operating systems provide the creationfile system, which is intended for
storing data on disks and providing
access to them.
Basic functions of the file system can be
divided into two groups:
File systems
Functions for working with files (creating,deleting, renaming files, etc.)
Functions for working with data that
stored in files (write, read, search
data, etc.)
File systems
To the file structure maintenance functioninclude the following operations taking place
under operating system:
creating and naming files;
creating directories (folders) and assigning them
names;
renaming files and directories
(folders); copying and moving files
between computer drives and between directories
(folders) of one disk;
File systems
deleting files and directories (folders);navigation by file structure with the aim of
access to a given file, directory (folder);
file attributes management.
Integrated Systems
Integrated packages area set of several software products,
combined into a single convenient tool.
The most developed of these include
text editor, organizer, electronic
table, DBMS, support tools
email, creation program
presentation graphics.
CASE technologies
CASE (Computer-Aided Software)Engineering - a set of tools and methods
software engineering for design
software that helps
provide high quality programs,
no errors and easy to maintain
software products. Also under CASE
understand a set of methods and means
design information systems With
using CASE tools.
CASE technologies
Development automation toolsprograms (CASE tools) - tools
automation of design processes and
software development for
systems analyst, software developer and
programmer
CASE technologies
analysis tools - designed forconstruction and analysis of a subject model
regions;
database design tools;
application development tools;
CASE technologies
process reengineering tools(fundamental rethinking and
radical redesign of business processes to achieve maximum
effect of production, economic and
financial and economic activities,
issued by the relevant
organizational, administrative and
regulatory documents. Reengineering
uses specific means
presentation and processing of problematic
information that is understandable to both managers and
developers of information systems.);
CASE technologies
planning and management toolsproject;
testing tools;
documentation tools.

Binding
Translation and subsequent steps to prepare a program for execution are the process of converting a program written in some formal language into another formal system - a computer architecture, in which it can be executed (interpreted). To understand this process, as well as the differences that exist in different programming languages, the concept of binding is introduced, as well as binding time.
Binding is the process of establishing correspondence between objects and their properties in a program in a formal language (operations, statements, data) and elements of computer architecture (commands, addresses).
Binding time The phase of preparing the program for execution (translation, linking, loading) at which this action is performed is called accordingly. Various characteristics the same object (for example, a variable) can be associated with different elements of the architecture at different times, that is, the binding process is not simultaneous.
Systemic software |
|

Possible binding times
When defining the language; when implementing a compiler;
during the broadcast, including:
when the preprocessor (macroprocessor) is running
during lexical, syntactic and semantic analysis, code generation and optimization;
during layout; while loading the program;
during program execution, including: when entering a module (procedure, function); at any point in the program execution.
System software |
|

Binding in int a,b; …a+b
The variable type int is an integer variable in a standard-length machine word (signed integer representation, two's complement code), associated with a similar form of data representation in a computer when defining a language.
The specific dimension of the int variable is determined by the implementation of the corresponding compiler.
The name a can be defined in a construct of the form
#define a 0x11FF . In this case, the name (pseudo-variable) is associated with its value in the first phase of translation - in the preprocessor.
System software |
|

Binding in int a,b; …a+b
If a variable is defined in the usual way as int a; then the binding of a variable to its corresponding type occurs during translation (at the semantic analysis phase).
If a variable is defined as external (global, outside the function body), then the meaning of its translation is to allocate memory for it in the program data segment, which is created for the current module (file). In this case, the binding of distributed memory to specific RAM is carried out in several stages:
System software |
|

Binding in int a,b; …a+b
during translation, the variable is bound to some relative address in the data segment of the object module (that is, its placement is fixed only relative to the beginning of the module).
When linking, data and command segments of various object modules are combined into a common program file, which is an image of the program's memory. In it, the variable already receives a relative address from the beginning of the entire program.
When a program is loaded into a certain memory area, it may not be located at the very beginning of this area. In this case, the addresses of variables specified in relative addresses from the beginning of the program module are linked to memory addresses, taking into account the movement of the program module.
System software |
|

Binding in int a,b; …a+b
if the program runs not in physical memory, but in virtual memory, then the loading process may be slightly different. A program module is conventionally considered to be loaded into a certain virtual address space (with or without moving both the entire program and its individual segments). The real loading of the program into memory is carried out already during the program’s operation in parts (segments, pages), and the matching (or linking) of virtual and physical addresses is carried out dynamically operating system using appropriate hardware.
System software |
|

Binding in int a,b; …a+b
If a variable is defined as automatic (local within the body of a function or block), then it is placed on the program stack:
during translation, its dimension is determined and commands are generated that reserve memory for it on the stack at the moment of entering the function body (block). That is, during translation, the variable is associated only with a relative address on the program stack;
The binding of a local variable to its address in the stack segment is carried out when executed at the moment of entering the body of the function (block). Thanks to this type of binding, there are as many “instances” of local variables in a recursive function as the number of times the function calls itself.
Slide 2
Memory organization
Physical memory that the processor has access to via the address bus is called RAM(or random access memory - RAM). RAM is organized as a sequence of cells - bytes. Each byte has its own unique address (its number), called a physical one.
The range of physical address values depends on the width of the processor address bus. For 80486 and Pentium it ranges from 0 to 232 - 1 (4 GB). For PentiumPro/II/III/IV processors this range is wider - from 0 to 236 - 1 (64 GB). The 8086 processor had 1 MB of memory with a twenty-bit address bus - from 0 to 220-1.
external memory
Slide 4
By the way, another name for a physical address is a linear address. This duality in the name is precisely due to the presence of a page model of the organization of RAM. These names are synonymous only when paging is disabled (in real mode, paging is always disabled). In the page model, linear and physical addresses have different meanings.
The memory management mechanism is entirely hardware and allows for: compact address storage in a machine instruction flexibility of the addressing mechanism protection of task address spaces in a multitasking system virtual memory support Slide 5 it can only execute one program at a time). However, at the same time, he can interrupt its execution at any time and switch to the procedure for processing an interrupt received from one of the peripheral devices. Any program that the processor is executing at this moment is allowed unlimited access to any areas of memory located within the first megabyte: to RAM - for reading and writing, and to ROM, of course, for reading only. The real processor operating mode is used in the MS DOS operating system, as well as in Windows systems 95 and 98 when loaded in MS DOS emulation mode.
Slide 6
In protected mode, the processor can run multiple programs simultaneously. In this case, each process (i.e., running program) can be assigned up to 4 GB of RAM. To prevent the mutual influence of running programs on each other, they are allocated isolated areas of memory. OSes such as MS Windows and Linux run in protected mode. In the virtual addressing mode of the 8086 processor, the latter actually operates in protected mode. For each task, its own is created virtual machine
, which allocates an isolated memory area of 1 MB in size and completely emulates the operation of an 80x86 processor in real addressing mode. For example, in the Windows 2000 and XP operating systems, a virtual machine of the 8086 processor is created every time the user starts a command interpreter window (MS DOS session).
Slide 7 Real addressing mode Distinctive features
The mechanisms for addressing physical memory in real mode are as follows: The range of changes in the physical address is from 0 to 1 MB, since only the 20 low-order bits of the address bus are used when addressing The maximum size of memory addressed using 16-bit registers is 64 KB To access a specific physical address Memory segmentation is used throughout all available RAM, i.e. splitting the available address space into 64 KB segments and using it instead of a physical logical address in the form:, i.e. combinations of segment start address and offset within the segment The 16-bit segment start address is placed in one of six segment registers (CS, DS, ES, SS, FS, or GS) Programs directly operate only on the 16-bit offset specified relative to the segment start
The least significant hexadecimal digit in the address of each segment is zero, i.e. the address of any segment will always be a multiple of 16 bytes; segment boundaries are located every 16 bytes of physical addresses. Each of these 16-byte fragments is called a paragraph.
Slide 9
Addresses specified in programs in the "segment-offset" form are automatically converted by the processor into 20-bit linear addresses during command execution according to the following scheme:
Slide 10
Example: byte given in the form segment-offset: 8000:0250 in hexadecimal.
Logical address: 8000:0250 ––––––––––––––––––––––––––––––– Segment: 80000 + Offset: 0250 ––––––– –––––––––––––––––––––– Physical Address: 80250 A typical program written for the 80x86 family of processors typically has three segments: code, data, and stack. When the program starts, their base segment addresses are loaded into the CS, DS and SS registers, respectively. In the three remaining registers ES, FS and GS, the program can store pointers to additional segments.
64 KB segments can overlap with other segments
Slide 12
Protected addressing mode When operating in protected mode, each program can be allocated a memory block of up to 4 GB in size, the addresses of which in hexadecimal notation can vary from 00000000 to FFFFFFFF. The program is said to be allocated a linear address space.
In secure mode, segment registers (CS, DS, SS, ES, FS, GS) store not 16-bit base addresses of segments, but selectors—pointers to segment descriptors located in one of the system descriptor tables. . Based on the information contained in the descriptor, the operating system determines the linear addresses of program segments. There are two types of tables: GlobalDescriptorTable (global descriptor table) and LocalDescriptorTables (local descriptor tables).
Slide 13
Descriptor 0 is illegal - it can be safely loaded into the segment register to indicate that the segment register is currently unavailable, but attempting to use it will generate an interrupt.
A typical program written for protected mode typically has three segments: code, data, and stack, information about which is stored in the three segment registers listed below. The CS register stores a pointer to a program code segment descriptor. The DS register stores a pointer to a program data segment descriptor. The SS register stores a pointer to a program stack segment descriptor.
Slide 15
The conversion of a selector-offset pair to a physical address is done as follows: If paging is disabled (via a bit in the global control register), the linear address is interpreted as a physical address and sent to memory for reading or writing. On the other hand, if paging is available, the linear address is interpreted as a virtual address and mapped to the physical address using a page table.
Slide 16
In protected mode, memory models are supported in hardware: FlatModel (flat, solid or linear model) - a memory organization in which all segments are mapped to a single linear address area. To achieve this, all segment handles point to the same memory segment, which corresponds to the entire 32-bit physical address space of the computer. For a flat model, at least two handles must be created, one for code references and one for data references.
. By setting the segment boundary to 4 gigabytes, the segmentation mechanism prevents exceptions from being thrown for memory references that span the segment boundary.
This model allows us to eliminate the segmentation mechanism from the system architecture, since all memory operations access a common memory space.
From a programmer's point of view, this model is the easiest to use, since a single 32-bit integer is enough to store the address of any variable or command.
Slide 19
MultisegmentedModel Each program has its own table of segment descriptors, called a Local Descriptor Table (LDT). In this case, it becomes possible for each process to create its own set of segments that do not intersect in any way with the segments of other processes. As a result, each segment is in an isolated address space.
Slide 20
The figure shows that each local descriptor table element defines a different memory segment. Each segment descriptor specifies its exact length. For example, a segment starting at address 3000 is 2000 bytes long in hexadecimal because the value of the segment descriptor field is 0002, and 0002x1000=2000. By analogy, the length of the segment starting at address 8000 is A000.
It should be noted that the Flat Model is implemented as a special case of a segmented model, when the program accesses a segment for which the entire linear space is allocated. Slide 21 Paging (page memory model) This model is a form of memory management for modeling a large, unsegmented address space using part
disk memory
and fragmented address space. Provides access to data structures that are larger than the size of available memory, storing them partly in RAM and partly on disk.
Under this model, the linear address space is divided into blocks of equal size (usually 4 KB), which are called pages.
The Page field is then processed as an index into the page table to find the physical address of the page block. To obtain the physical address of the required byte or word, the last Offset field is added to the page block address. As a result, you can easily make sure that the total amount of RAM used in all programs running on the computer exceeds the amount of real computer memory. That is why page memory organization is often called virtual memory (virtual memory). The performance of the virtual memory system is ensured by special program
, which is part of the operating system called the virtual memory manager.
Slide 24
Paging memory organization solves the problem of memory shortage in the best possible way. The fact is that before starting execution, any program must be loaded into RAM, the size of which is always limited (for example, due to the design features of the computer or the price of the memory module). Computer users usually load several programs into memory at once so that they can switch between them while working (for example, move from one window to another). On the other hand, the volume of disk memory is much greater than the volume of computer RAM, and besides, this memory is much cheaper. Therefore, by using disk memory when using paged memory organization, the user gets the impression that he has an unlimited amount of RAM. Of course, you have to pay for everything: the access speed of disk memory is several orders of magnitude lower than that of RAM.
or data, and loads it into a free area of RAM.
The topic of protection is closely related to virtual memory. Pentium supports four security levels, with Level 0 being the most privileged and Level 3 being the least privileged. At each moment in time, the running program is at a certain level. Each segment in the system also has its own level.
Slide 27
At level 0 is the operating system kernel, which handles input/output processing, memory management, and other primary issues. At level 1 – system call handler. User programs at this level can access procedures to make system calls, but only a specific and protected list of procedures. Level 2 contains library procedures, possibly shared by multiple running programs. User programs can call these procedures and read their data, but cannot change them. Finally, user programs run at level 3, which has the least security level.
View all slides
Description of the presentation by individual slides:
1 slide
Slide description:
2 slide
Slide description:
Software is a set of commands that control the operation of a computer. Without software, a computer will not be able to perform the tasks we typically associate with computers. The functions of the software are as follows: manage the organization’s computer resources; provide the user with all the tools necessary to benefit from these resources; act as an intermediary between organizations and stored information. Selecting software that meets the needs of the organization is one of the key tasks of management personnel. .
3 slide
Slide description:
4 slide
Slide description:
System support is a set of programs that provide component management computer system. System software includes: operating systems, network software, command and file processors (shells), programming languages, service programs (test and diagnostic programs, system peripheral device drivers, utilities), archivers and anti-virus programs. .
5 slide
Slide description:
6 slide
Slide description:
Basic software is a set of programs that ensure the operation of a computer. The basic software includes: operating systems, operating shells (shell). Operating system (OS) is the program that is first loaded when you turn on your computer. The first OS for an IBM-compatible computer (MS DOS) was created in 1981. The OS organizes the execution of other programs. Without it, human work on a computer is impossible. The OS manages the computer, its resources (RAM, disk space, etc.), launches service functions, and controls operation technical devices and some auxiliary programs, carries out a dialogue with the user, launches application and other programs. Operating systems are the main software systems that perform the following main functions: 1) testing the performance of the computer system and setting it up upon initial startup; 2) ensuring synchronous and effective interaction of all hardware and software components of the computer system during its operation; 3) ensuring effective user interaction with computing system. OS are classified into: · single-user, single-tasking systems (MS-DOS, etc.); ·single-user multitasking systems (OS/2, Windows 95/98/2000, etc., Vista); ·multi-user (network) systems (UNIX family, Linux, WindowsNT, etc.). The main functions of network operating systems designed to work in various networks include: directory and file management; protection against unauthorized access; ensuring fault tolerance; network management. The simplest network operating systems are peer-to-peer operating systems. Their function is to divide the disks of different nodes between all users, enforce passwords and prohibitions on the use of certain disks.
7 slide
Slide description:
Operating shells are an interface for user interaction with the operating system. Operating shells interpret (translate into machine code and execute) OS commands. Types of operating shells: graphical - for entering OS commands through menus, switches, buttons, presented in the form of graphic images ( Windows Explorer, which includes the Desktop, Start Menu, Taskbar, and file manager) Text command line- to enter OS commands from the keyboard (cmd.exe, Windows PowerShell, included in MS Windows OS) packages - for recording a sequence of OS commands into a file (file with the extension .bat), then the file is interpreted. windows - for entering OS commands through menus, switches, buttons, presented in the form of a set of letters, numbers and pseudographic symbols.
8 slide
 Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned
Order 343 mail. Order by Russian post. Consequences of failure to appear in court when summoned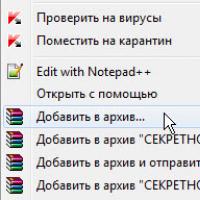 How to put a password on a folder on a Windows computer without and with programs
How to put a password on a folder on a Windows computer without and with programs Pluton – Free Bootstrap HTML5 One Page Template
Pluton – Free Bootstrap HTML5 One Page Template History of ZX Spectrum: Myths and reality New Spectrum
History of ZX Spectrum: Myths and reality New Spectrum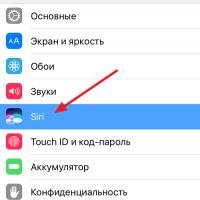 Voice assistant Siri from Apple Siri functions on iPhone 6s
Voice assistant Siri from Apple Siri functions on iPhone 6s How to roll back to a previous version of iOS?
How to roll back to a previous version of iOS?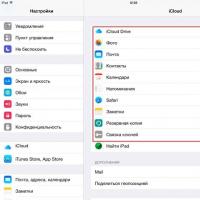 Unlock iPad in four days
Unlock iPad in four days